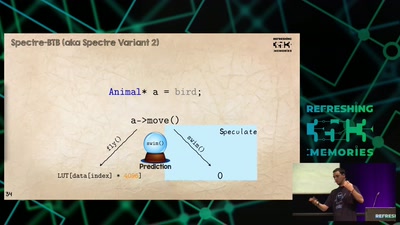
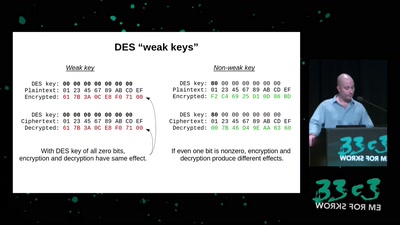
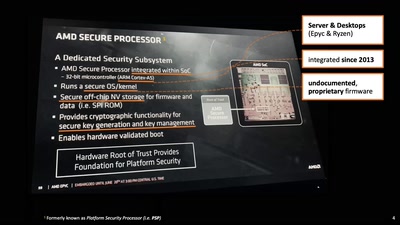
Events for tag "Security"
70 min
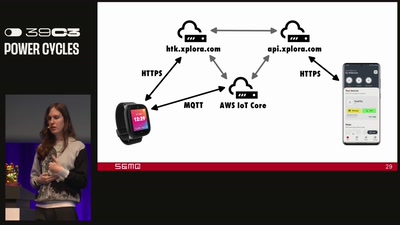
Attacking IoT Telemetry
A study of weaknesses in the pipeline of rapidly advancing…
56 min
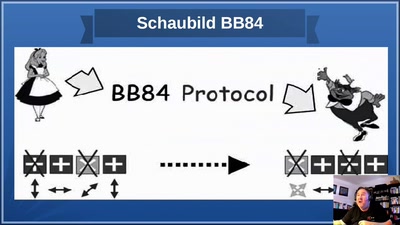
God does not play dice!
an introduction to quantum cryptography for sysadmins and…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

48 min
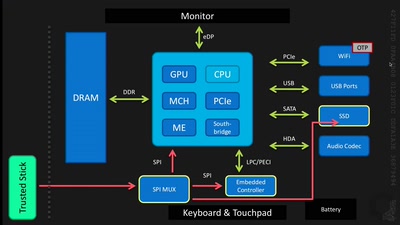
Architecture of secure IoT devices
Security by design
59 min
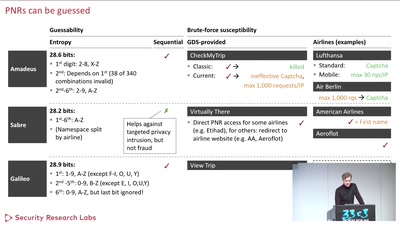
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways
47 min
Enterprise Mail-Security mit Open-Source?
Rspamd - Mail-Security-Framework
58 min
Linux Host Security
Lessons Learned & Praxistipps

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

36 min
Modchips of the State
Hardware implants in the supply-chain

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
61 min
Email authentication for penetration testers
When SPF is not enough

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

51 min
Smart Home - Smart Hack
Wie der Weg ins digitale Zuhause zum Spaziergang wird

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system
61 min
wallet.fail
Hacking the most popular cryptocurrency hardware wallets

61 min
DANEn lügen nicht
SSL/TLS Zertifikate mit DNSSEC absichern

60 min
Beyond your cable modem
How not to do DOCSIS networks

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

60 min
Hardware-Trojaner in Security-Chips
Eine Reise auf die dunkle Seite

39 min
Tales of old: untethering iOS 11
Spoiler: Apple is bad at patching

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

47 min
The Freenet Project
Anonymes Netzwerk basierend auf dem Kleine-Welt-Phänomen

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

59 min
Provable Security
How I learned to stop worrying and love the backdoor
46 min
IT-Sicherheit in vernetzten Gebäuden
Was kann man noch retten, wenn langlebigen Strukturen…

53 min
Console Hacking 2016
PS4: PC Master Race

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…
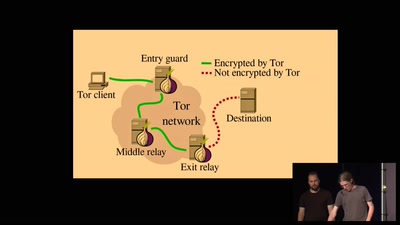
47 min
Introduction to Mix Networks and Katzenpost
a new anonymity movement
35 min
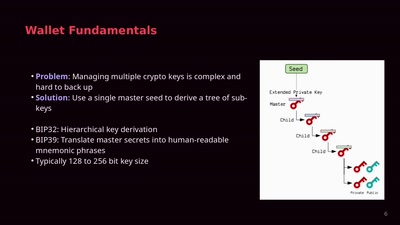
Wallet Security
How (not) to protect private keys

41 min
Ten Years of Rowhammer:
A Retrospect (and Path to the Future)

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

61 min
Nintendo Hacking 2016
Game Over
58 min
IT-Unsicherheit in der Gebäudeautomation
Eine Bestandsaufnahme
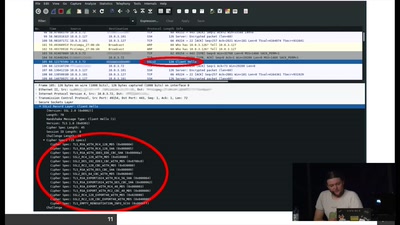
30 min
Mit dem Getränkeautomaten in die Cloud
Über die (Un-)Sicherheit eines Bezahlsystems
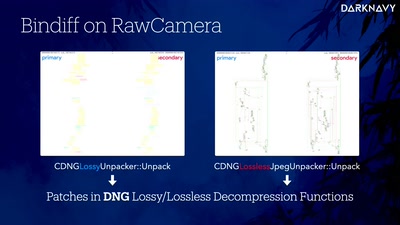
52 min
DNGerousLINK
A Deep Dive into WhatsApp 0-Click Exploits on iOS and…

31 min
TrustZone is not enough
Hijacking debug components for embedded security

54 min
Sichere Softwareentwicklung
Ein praktischer Einstieg
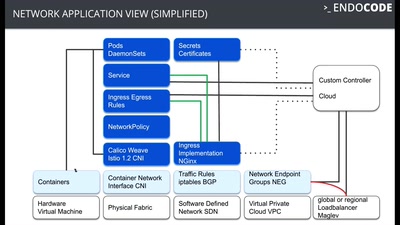
43 min
Hacking Containers and Kubernetes
Exploiting and protecting containers with a few lines of…

55 min
Who is attacking you?
Open source router that catches the attackers
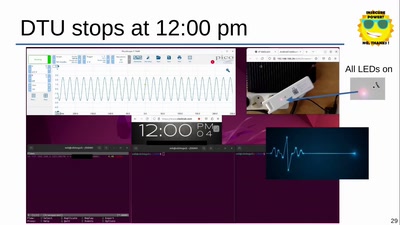
39 min
Decentralized energy production: green future or cybersecurity nightmare?
The cybersecurity dark side of solar energy when clouds are…

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…
36 min
Unlocking the Road Ahead: Automotive Digital Forensics
A deep dive into an underrepresented research area

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution
42 min
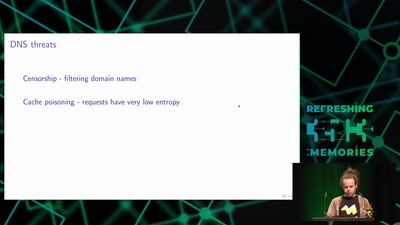
Domain Name System
Hierarchical decentralized naming system used since 30 years

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…
65 min
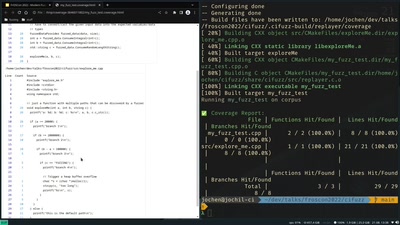
Introduction to modern fuzzing
Find and fix vulnerabilities before they reach production.
60 min
Build your own NSA
How private companies leak your personal data into the…

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

29 min
Building and Breaking Wireless Security
Wireless Physical Layer Security & More...

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

53 min
Cryptography demystified
An introduction without maths

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy
37 min
Code BROWN in the Air
A systemic update of sensitive information that you sniff…
57 min
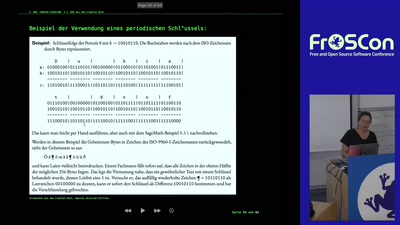
SageMath Examples from the CrypTool Book
50% Talk 50% Live-Session to try out some code yourself

52 min
SiliVaccine: North Korea's Weapon of Mass Detection
How I Learned to Stop Worrying and Love the Backdoor

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

40 min
Verlorene Domains, offene Türen
Was alte Behördendomains verraten

56 min
Viva la Vita Vida
Hacking the most secure handheld console

43 min
Anykernels meet fuzzing
how to make NetBSD a better software for you and me

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation

41 min
Build a Fake Phone, Find Real Bugs
Qualcomm GPU Emulation and Fuzzing with LibAFL QEMU

60 min
What the PHUZZ?!
Finding 0-days in Web Applications with Coverage-guided…
54 min
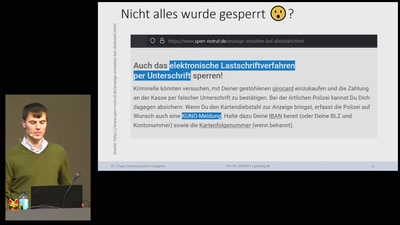
Oh no: KUNO - Gesperrte Girocards entsperren
Über „Girodays“ & anderen Kuriositäten
41 min
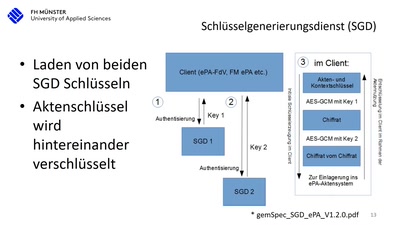
15 Jahre deutsche Telematikinfrastruktur (TI)
Die Realität beim Arztbesuch nach 15 Jahren Entwicklung…
53 min
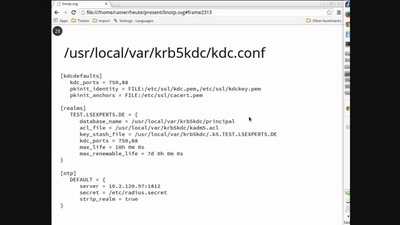
LinOTP und Single Sign On
Zwei-Faktor Authentisierung in der Praxis

60 min
Cybersicherheit in der Gesellschaft
Die Rolle des CRA für Freie Software

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…
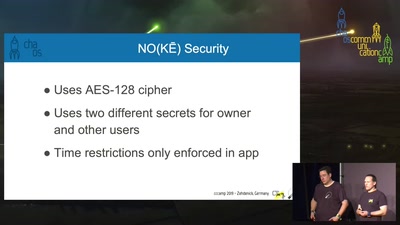
46 min
Taking Bluetooth lockpicking to the next level
...or the 37th floor of a Hotel

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs
47 min
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide
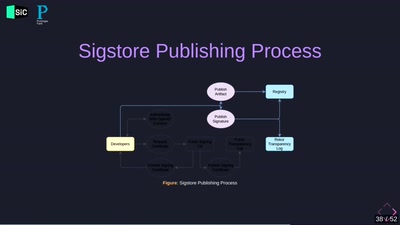
33 min
The new old: Supply Chain Security
(with Kubernetes this time)

55 min
The DROWN Attack
Breaking TLS using SSLv2
56 min
Console Security - Switch
Homebrew on the Horizon

38 min
What your phone won’t tell you
Uncovering fake base stations on iOS devices

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…
43 min
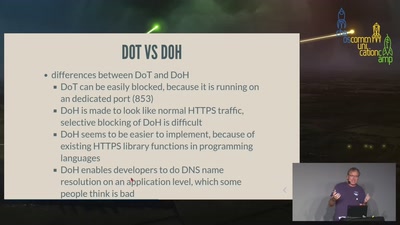
DoH or Don't
The dilemma of DNS privacy protocols
39 min
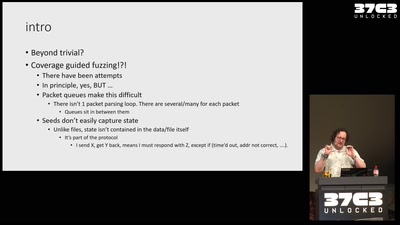
Fuzzing the TCP/IP stack
beyond the trivial
58 min
Are all BSDs created equally?
A survey of BSD kernel vulnerabilities.

60 min
Lets break modern binary code obfuscation
A semantics based approach

42 min
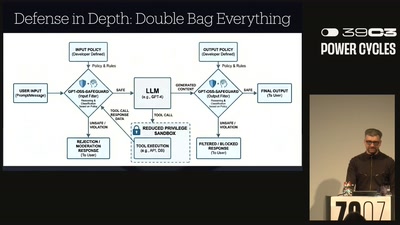
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…
58 min
Operation Triangulation
What You Get When Attack iPhones of Researchers

56 min
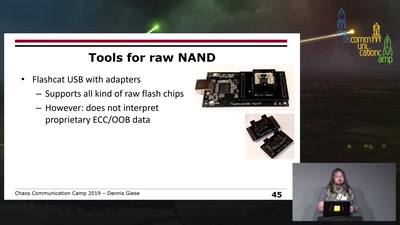
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…
31 min
DPRK Consumer Technology
Facts to fight lore
67 min
"Früher oder später erwisch ich euch alle!"
Eine Einführung in die digitale Forensik und ihre…

60 min
Windows drivers attack surface
some 'new' insights
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

41 min
Fighting back against Libra - Decentralizing Facebook Connect
Nym Anonymous Authentication Credentials

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

72 min
Console Hacking
Breaking the 3DS

58 min
Freedom of Forking
Multi Faktor Authentifizierung mit eduMFA
65 min
LatticeHacks
Fun with lattices in cryptography and cryptanalysis

42 min
Nintendo hacking 2023: 2008
Finishing off the Nintendo DSi

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

46 min
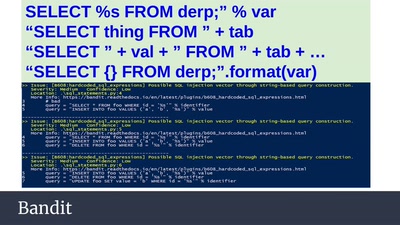
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
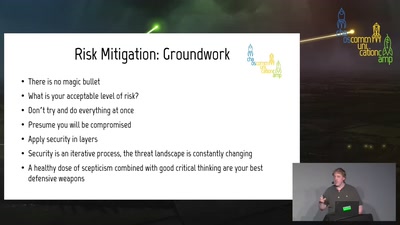
41 min
Introduction to (home) network security.
A beginner-friendly guide to network segmentation for…

39 min
Venenerkennung hacken
Vom Fall der letzten Bastion biometrischer Systeme

58 min
PLC-Blaster
Ein Computerwurm für PLCs

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…
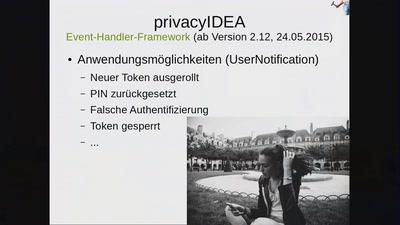
59 min
Mehr-Faktor-Authentifizierung am Puls der Zeit
Was ist neu in privacyIDEA
41 min
The long road to reproducible builds
why+how to create bit by bit identical binary packages
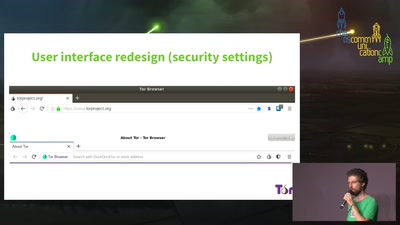
43 min
Updates from the Onion
The Road to Mobile Tor and Improved Censorship Circumvention
52 min
Turris: secure open source router
Who is the root on your router?

37 min
OpenVPN im Unternehmenseinsatz
Realisierung einer Hochverfügbarkeitslösung mit dynamischem…

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

43 min
Hirne Hacken
Menschliche Faktoren der IT-Sicherheit

56 min
How not to use OAuth
New security recommendations for OAuth
62 min
Einführung in Smartphone Malware Forensik
Wie man Stalkerware und Staatstrojaner auf Smartphones…
56 min
Running your own 3G/3.5G network
OpenBSC reloaded

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…
49 min
SD-WAN a New Hop
How to hack software defined network and keep your sanity?

38 min
Wir wissen wo dein Auto steht
Volksdaten von Volkswagen

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

45 min
AppArmor Crashkurs
Lerne in unter einer Stunde, AppArmor-Profile zu erstellen…

40 min
Fuzz Everything, Everywhere, All at Once
Advanced QEMU-based fuzzing

41 min
Back in the Driver's Seat
Recovering Critical Data from Tesla Autopilot Using Voltage…

62 min
radare demystified
after 1.0
57 min
Cloud Storage Encryption with Cryptomator
Cryptomator is a multi-platform, client-side encryption…

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge
59 min
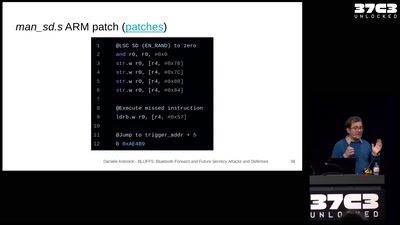
BLUFFS: Bluetooth Forward and Future Secrecy Attacks and Defenses
Breaking and fixing the Bluetooth standard. One More Time.

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

57 min
To Make Hearts Bleed
A Native Developer's Account On SSL
63 min
sectpmctl für LUKS Full Disk Encryption (FDE)
Secure Boot und TPM gestützte LUKS…
51 min
Automatisierung im Cyberspace
Wie wir die Asymmetrien überwinden können

46 min
It's not safe on the streets... especially for your 3DS!
Exploring a new attack surface on the 3DS
38 min
A deep dive into the world of DOS viruses
Explaining in detail just how those little COM files…

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

59 min
Die DSGVO als Chance nutzen
Ein Fahrplan für ein mehr an Informationssicherheit in…

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)
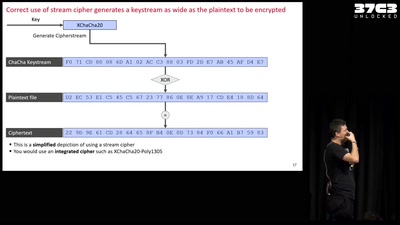
40 min
Unlocked! Recovering files taken hostage by ransomware
Decrypting files hijacked by the "second most used…
61 min
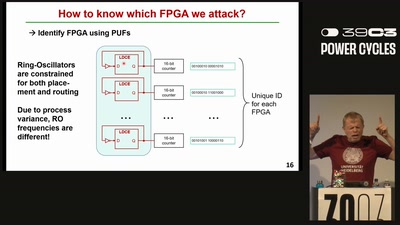
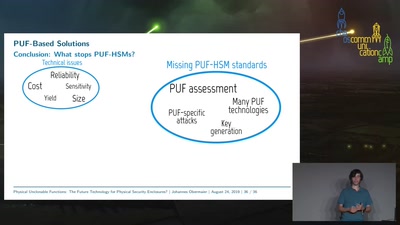
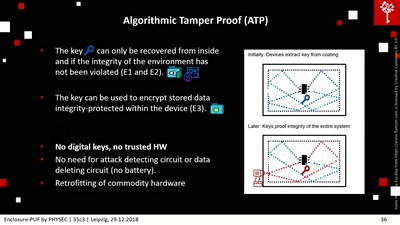
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
60 min
The Perl Jam 2
The Camel Strikes Back

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people
60 min
Ghidra - An Open Source Reverse Engineering Tool
How the NSA open-sourced all software in 2019

51 min
How to drift with any car
(without your mom yelling at you)

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

25 min
Wie man mit Mathematik ein API übernehmen kann
(und wie gute Architektur das verhindert)

49 min
Automated security testing for Software Developers who dont know security!
secure your apps and servers through continuous integration

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP

46 min
Beyond the Pile of Knobs
Redesigning NoScript’s UX

63 min
Web-App-Encryption
Is your data secure by default? How Django can be used to…
38 min
ARMore: Pushing Love Back Into Binaries
Aarch64 binary rewriting adventures but mostly pains
46 min
What The Fax?!
Hacking your network likes it's 1980 again

60 min
Shopshifting
The potential for payment system abuse

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…
59 min
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…

49 min
Kerberos und OTP
Nur einmal authentisiert - aber stark!
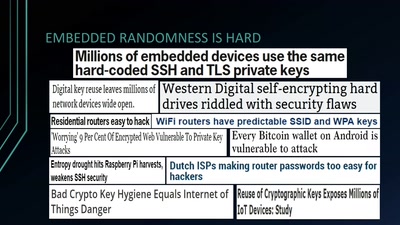
36 min
Wheel of Fortune
Analyzing Embedded OS Random Number Generators
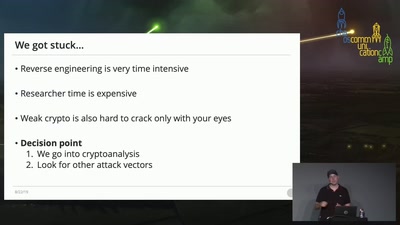
44 min
500.000 Recalled Pacemakers, 2 Billion $ Stock Value Loss
The Story Behind
61 min
Container for Desktops
Security und Privacy mit LXC et.al. - auch auf…
59 min
Develop Secure Software - The DevGuard Project
OSS Security von Entwicklern für Entwickler

44 min
ASLR on the line
Practical cache attacks on the MMU

44 min
TAPS Transport Services API
Retiring the BSD Socket API
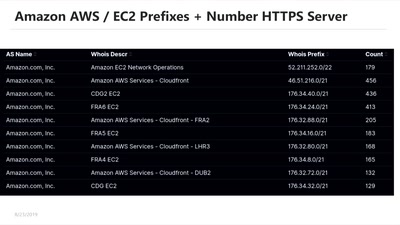
42 min
Fast Global Internet Scanning - Challenges and new Approaches
Or how to become your own ISP

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster
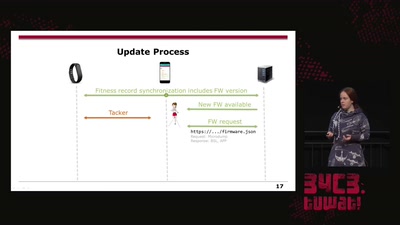
22 min
Doping your Fitbit
On Fitbit Firmware Modifications and Data Extraction

31 min
A Tale of Two Leaks:
How Hackers Breached the Great Firewall of China
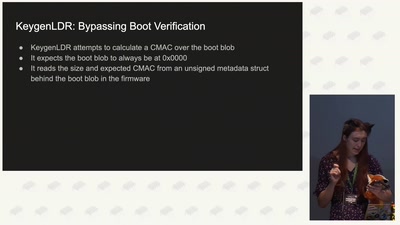
39 min
Breaking the black-box security coprocessor in the Nintendo Switch
a story of vulnerability after vulnerability

46 min
Writing secure software
using my blog as example

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

33 min
Gone in 60 Milliseconds
Intrusion and Exfiltration in Server-less Architectures

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…
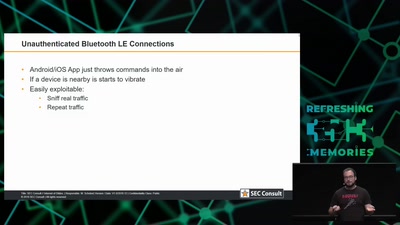
32 min
Internet of Dongs
A long way to a vibrant future

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks
52 min
Leaving legacy behind
Reducing carbon footprint of network services with MirageOS…
37 min
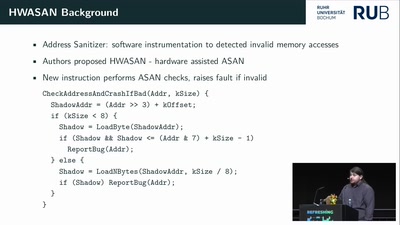
Inside the AMD Microcode ROM
(Ab)Using AMD Microcode for fun and security
60 min
Unpatchable
Living with a vulnerable implanted device
52 min
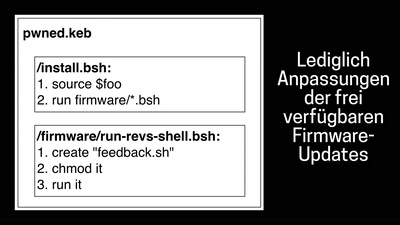
Ladeinfrastruktur für Elektroautos: Ausbau statt Sicherheit
Warum das Laden eines Elektroautos unsicher ist

40 min
ACE up the sleeve:
Hacking into Apple's new USB-C Controller

36 min
Who cares about the Baltic Jammer?
Terrestrial Navigation in the Baltic Sea Region
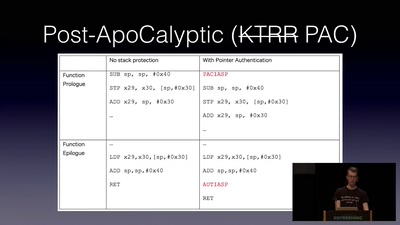
47 min
Jailbreaking iOS
From past to present

57 min
Du kannst alles hacken – du darfst dich nur nicht erwischen lassen.
OpSec für Datenreisende
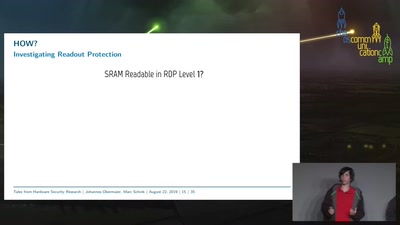
45 min
Tales from Hardware Security Research
From Research over Vulnerability Discovery to Public…

61 min
All Your Gesundheitsakten Are Belong To Us
"So sicher wie beim Online-Banking": Die elektronische…

58 min
Skynet Starter Kit
From Embodied AI Jailbreak to Remote Takeover of Humanoid…
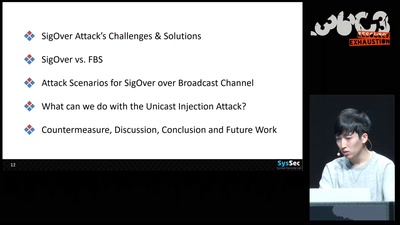
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications

41 min
Why Railway Is Safe But Not Secure
Security Of Railway Communication Protocols

40 min
Domain computers have accounts, too!
Owning machines through relaying and delegation

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom

59 min