30 min
Was die Sensor & Automatisierungstechnik in der…

57 min
How does the CCC run a conference?
31 min
Ein Leitfaden für post-humane Computer- und…
30 min
Afrofuturism, Telling tales of speculative futures
62 min
An introduction to the basics of climate research and what…

59 min
Zum Verbot von Indymedia linksunten

33 min
Eine Geschichte voller Missverständnisse
58 min
A survey of BSD kernel vulnerabilities.

44 min
Practical cache attacks on the MMU

55 min
Towards an open source binary firmware analysis framework
61 min
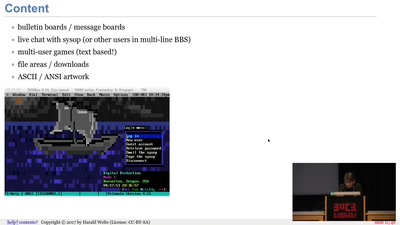
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

61 min
Über die Banalität der Beeinflussung und das Leben mit…

31 min
How the internet self-governs without international law
29 min
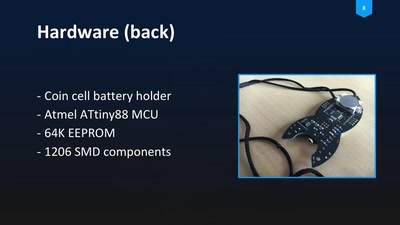
How to make a community project fly

31 min
Resilient P2P Messaging for Everyone

58 min
An Exploration of NFC Transactions and Explanation How…
56 min
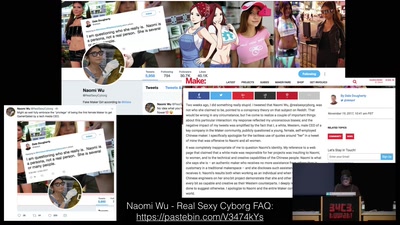
Obsolete Technologies + Critical Material Studies in Media…
53 min
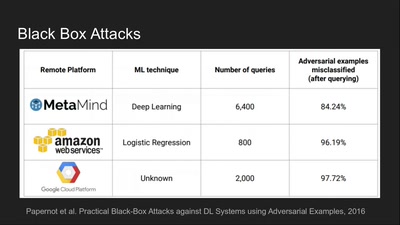
Tools for Fooling the "Black Box"

31 min
Things you always wanted to know about NIC drivers

29 min
Wird es Regen geben? Ein Ausblick auf die neue…

55 min
Analyse einer Wahlsoftware
21 min
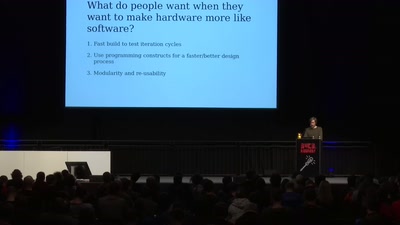
Is designing circuits with code instead of CAD the future…

61 min
Die Informatik löst formale (mathematisch modellierte)…

32 min
Wie in Österreich über Sicherheit und Überwachung…
33 min
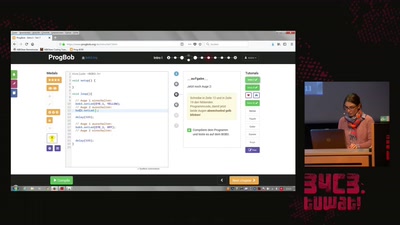
5.-Klässlerinnen, die über die Millisekunden für einen…

63 min
Artistic interventions in climate change
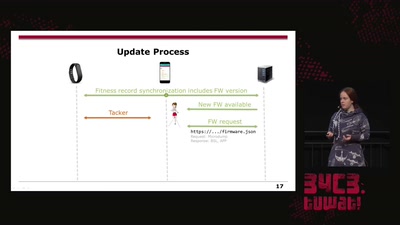
22 min
On Fitbit Firmware Modifications and Data Extraction

29 min
Shipped from Germany for 0.1412554 Bitcoins

61 min
Von Technik, Kollaborationen und Erreichtem zum G20-Gipfel…

30 min
Open Source Hardware for Smart Candies

49 min
Ways to Chaos in Digital and Analogue Electronics

56 min
A journey on how to fix broken proprietary hardware by…

29 min
was alles geht und wie man anfängt, mit Mikroskopen

57 min
An introduction into reverse-engineering x86 microcode and…

31 min
Political pressure for DNA-based facial composites

59 min
Exposing the global banking watchlist

43 min
Forensic Architecture is an independent research agency…
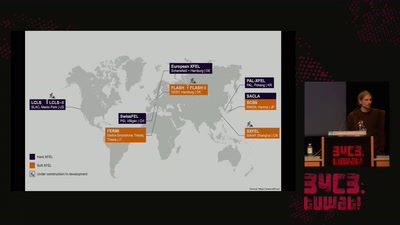
59 min
...or why we need 17 billion Volts to make a picture.

32 min
Forcing the Netherlands to publicly debate privacy and the…
39 min
China's Social Credit Systems
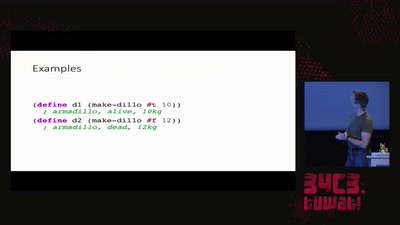
31 min
From Hacker Culture to the Software of the Future
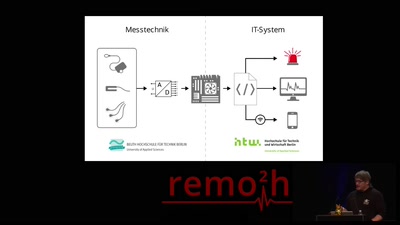
35 min
mit Krisenintervention den Kapitalismus hacken

32 min
From tractors to Web standards
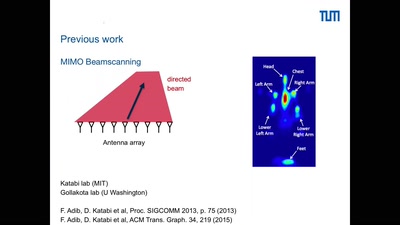
61 min
Can we see the stray radiation of wireless devices? And…

28 min
Theory and practice of moonshining and legal distilling

61 min
Survey of Network Anonymisation Techniques

58 min
CITL: Quantitative, Comparable Software Risk Reporting

51 min
(without your mom yelling at you)

33 min
Rosa Menkman investigates video compression, feedback, and…

50 min
Overview of how the state censored and how it got…

27 min
Research on Monitoring Italian Government Surveillance…
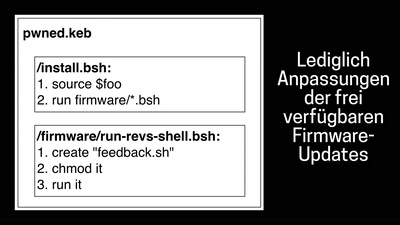
52 min
Warum das Laden eines Elektroautos unsicher ist
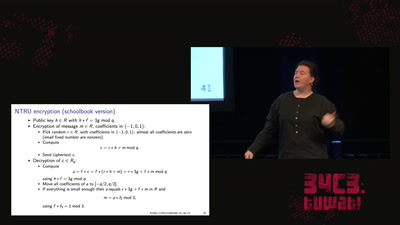
65 min
Fun with lattices in cryptography and cryptanalysis

60 min
A semantics based approach
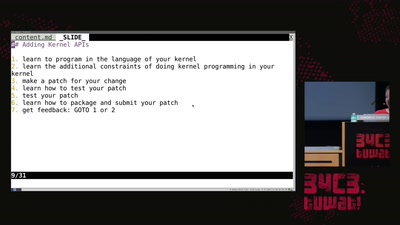
32 min
reject the default reality^W abstractions and substitute…
55 min
Die EU hat die Wahl: Schutz von Menschen oder von…
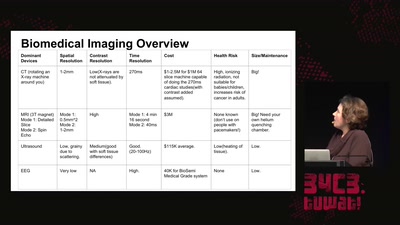
35 min
An Open Electrical Impedance Tomography Project

115 min
Die Wissenschaftsgala vom 34C3
30 min
Wie man ein Haus kaufen kann ohne es zu besitzen

32 min
A decentralized Public Key Infrastructure that supports…

60 min
A critical look on a new audio Format
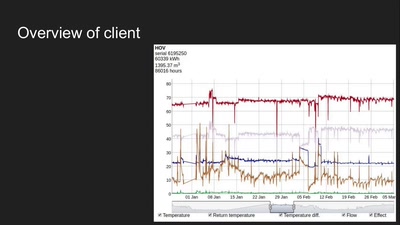
30 min
Freetown Christiania´s digitally controlled/surveyed…

47 min
Die aktuellen Auseinandersetzungen über digitale…

107 min
Die geekige Wort- & Bilderrätselspielshau ist zuЯück

30 min
The Open Observatory of Network Interference
60 min
'Liberating' Firmware from Closed Devices with Open Source…
31 min
is there no such thing as open hardware?

58 min
From molecular colonization to molecular collaboration

59 min
The Bundestagswahl 2017 and Rise of the AfD

46 min
Strong metadata protection for asynchronous messaging

58 min
Traveling with Digital Devices in the Golden Age of…

25 min
The time travelling android isn’t even our biggest problem

32 min
Raum, Zeit, Licht und Gravitation, wie hängt das zusammen?

42 min
Dissecting FPGAs from bottom up, extracting schematics and…

33 min
The Robots Play Our Music and What Do We Do?
28 min
Satellite Open Ground Station Network
45 min
Hacking industrial control gateways

38 min
from apple to schnaps -- a complete diy-toolchain

30 min
Informationsfreiheit trotz CSU

30 min
How much can we trust science in light failed replications,…
35 min
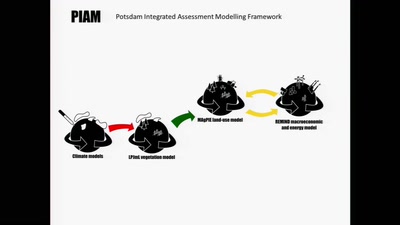
Cybernetic models analyze scenarios of interactions between…
66 min
Therapiestunde mit einem Datenjournalisten und vielen…

34 min
How the reputation economy is creating data-driven…

46 min
Analyzing & Breaking Exploit Mitigations and Secure Random…
58 min
Get a unique tour of some of the world’s most unusual…
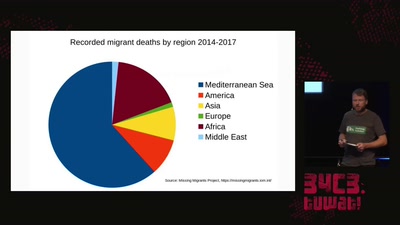
32 min
How search and rescue in the mediterranean was criminalized

66 min
A Rapidly Emerging Police State and Imminent Deportation to…

32 min
On the obstacles to think of emergent technologies in the…

43 min
Analysing the terminology of the UK’s Snooper’s Charter

60 min
Neues vom Zentrum für Politische Schönheit
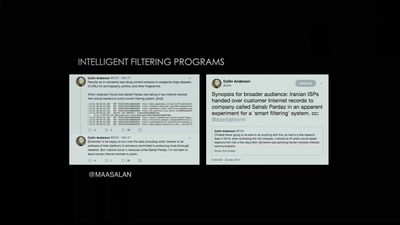
47 min
The Situation of Censorship and Surveillance in Iran, and…
48 min
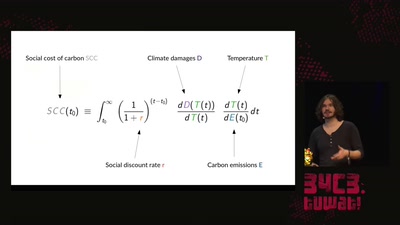
Wieviel CO2 macht <...>? Ungefähr?
61 min
Wie die Überwachung unsere Sicherheit gefährdet

31 min
Hijacking debug components for embedded security

58 min
How Undocumented Immigrants in the US Navigate Technology

51 min
An AES encrypted radio system
31 min
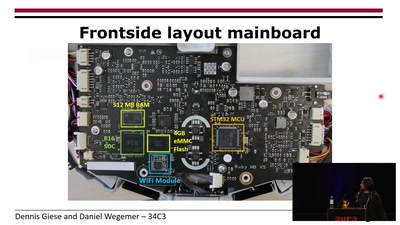
Why is my vacuum as powerful as my smartphone?

33 min
Going to space the libre way

32 min
Approaches to working with sound and network data…

59 min
Shamir secret sharing: How it works and how to implement it

31 min
Walter Höllerer bei WikiPedia

32 min
...and dehumanize ourselves in the process?

31 min
Decrypting French encryption law

61 min
Das erste computer netzwerk in Krieg (Jugoslavia 1992-1997)