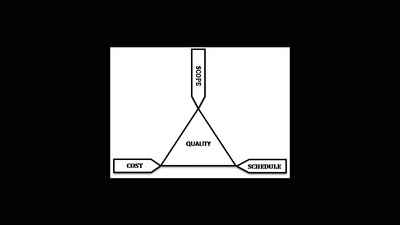
25 min
Destroying data as a performative act

28 min
or how we learned to stop worrying and love the NSA
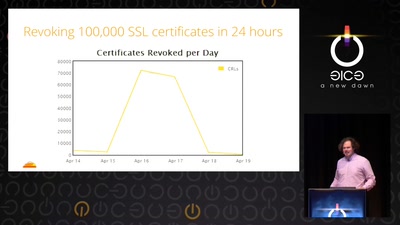
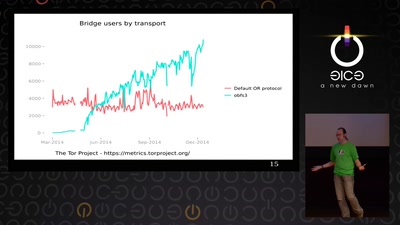
29 min
The untold story of what really happened, how it was…
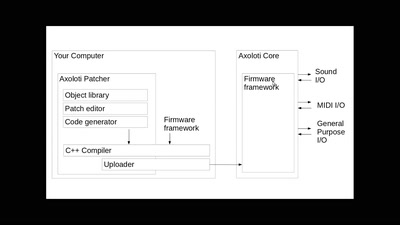
29 min
DIY audio signal processing

29 min
Several failure modes of the hacker scene

30 min
How governments use censorship and surveillance as part of…

30 min
Exploring identity and empathy through neuroscience,…

30 min
A Bus Trip into the Surveillance Culture of Berlin One Year…

30 min
Reversing the Surveillance Business Model

30 min
Creating an open source secure flash-drive-sized computer
30 min
How speech processing helps the CCC subtitle project, and…

31 min
Verteidigung gegen Dunkle Künste
31 min
From war pigeons in 1914 to cyborg moths in 2014

31 min
Lessons learned from crowdfunding a hardware project
31 min
Wie es kommt, dass technischer Fortschritt den Nutzern…
32 min
Augmenting the Human Mind

32 min
Automatic detection of key-reuse vulnerabilities
33 min
A view into technology on the other side of the world

33 min
Neue Energie für die Informationsfreiheit

33 min
Reports from the Frontlines

34 min
Einstellungen und Internetnutzungsverhalten im Kontext des…

35 min
Trends in the sanitarian territory
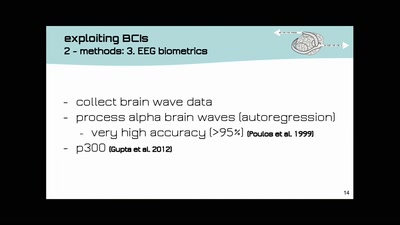
38 min
open source DIY brain-computer-interfaces | technology and…
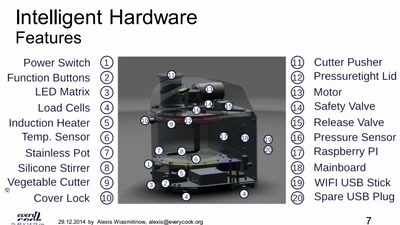
39 min
We want all data about food to be linked and public

39 min
The next big privacy heist

45 min
Das Duo 'read & delete' präsentiert radikale philosophische…
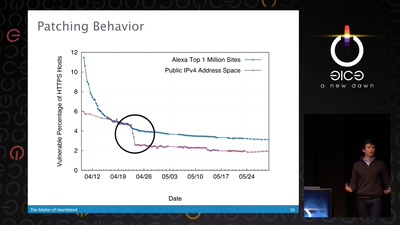
50 min
What went wrong, how the Internet reacted, what we can…

50 min
An open-hardware bipedal walking machine

53 min
How 150 year old equations still help to communicate

54 min
Do you care about Matroshka processors?

54 min
Wir leben noch und zwar sehr gut.

55 min
Turning copyright upside-down with metadata

55 min
The story of the NSA listening post – told by an ex-SIGINT…

55 min
A gentle introduction to elliptic-curve cryptography

55 min
New Bleichenbacher Side Channels and Attacks
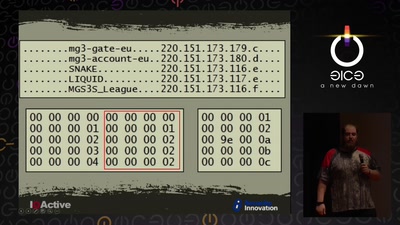
55 min
Reverse Engineering Dead Protocols

55 min
Too Much Fun with Microwaves

57 min
or having FUN with (home/hackerspace) robotics

58 min
Industrial System Ownership

58 min
Die Krise der Politik ist die Krise der Bilder

58 min
From the Outside Looking In

58 min
A Historical Re-Enactment of the PayPal14

58 min
A Journey to Coax Out Chips' Inner Secrets
59 min
FPGAs for Everybody with Novena
59 min
Vortrag mit aktuellen Fotos aus luftigen Perspektiven

59 min
A Lawful Method for Converting Closed IP into Open IP
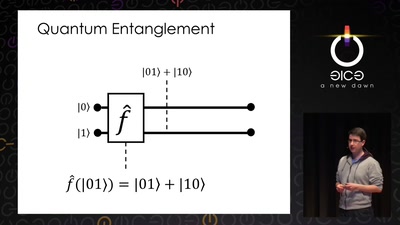
59 min
Understanding the architecture of a quantum processor

60 min
Piecing together the missing bits

60 min
Und nichts (Secure) Bootet mehr?

60 min
Gefahren von Kameras für (biometrische)…

60 min
An overview of usable security research

60 min
Taking stock after two years of net neutrality in the…

60 min
Evaluating a complex cryptographic implementation

60 min
Using microcontrollers to capture the blink of an eye for…

60 min
One Terabyte of Kilobyte Age

60 min
How computation helps to explain mind, universe and…

60 min
You have a tracking device in your pocket

60 min
Operative Kommunikation im digitalen Informationskrieg

61 min
Cybernetics, Anti-Terrorism, and the ongoing case against…

61 min
fun(ctional) operating system and security protocol…

61 min
Developing the Future of Authenticated Encryption
61 min
Exploitation in a new media

61 min
European copyright reform is finally on the horizon
61 min
Politics and Physics of a Problem That's Not Going Away

61 min
... or how we battle the daemons of memory safety

61 min
Internet reengineering session
61 min
A Deep Technical Analysis

61 min
Techniques for Chip Preparation

62 min
Der Protest gegen TTIP und CETA

62 min
The art of making a free phonebox and the culture of…

62 min
A Free Robotic Certificate Authority

62 min
A century of secret deals between the NSA and the telecom…

62 min
Die digitale „Agenda“ der Bundesregierung aus inhaltlicher,…

63 min
"Bei Kopierern kommt das raus, was man reinsteckt." – Wer…

63 min
how the EU was hypnotised that the NSA did not exist

63 min
transparency in the service of justice

63 min
Moving Beyond Single Points of Failure for Software…

64 min
The Role of Stylometry in Privacy

64 min
post-existentialism is the question, not post-privacy
65 min
First steps into space with sounding rockets

67 min
How many windows are open in the patent fortress

67 min
Jahresupdate zur GEMA-Alternative C3S
67 min
Das Zentrum für politische Schönheit

69 min
How to make your own telescope

95 min
Ein Science-Fiction-Theaterstück

101 min
Damit Sie auch morgen schlecht von Ihrem Computer träumen.

117 min
Wir helfen Euch die Fnords zu sehen.