65 min
The exhaust emissions scandal („Dieselgate“)
Take a deep breath into pollution trickery

61 min
Quantenphysik und Kosmologie
Eine Einführung für blutige Anfänger
62 min
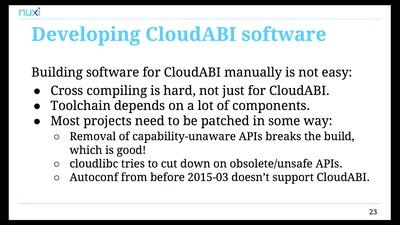
Wie man einen Blackout verursacht
und warum das gar nicht so einfach ist.

69 min
Grundrechte gelten nicht im Weltall!
Die absurdesten Szenen aus dem…
128 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 32C3

60 min
Beyond your cable modem
How not to do DOCSIS networks

61 min
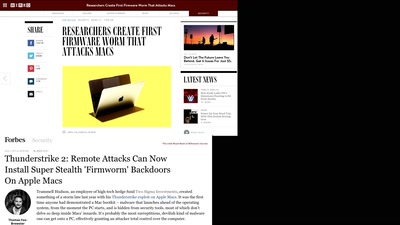
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.
95 min
Hacker Jeopardy
Zahlenraten für Geeks
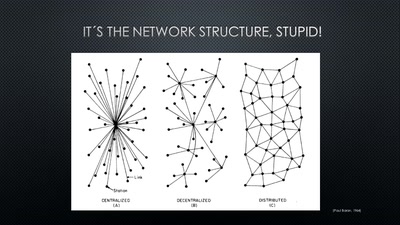
62 min
A New Kid on the Block
Conditions for a Successful Market Entry of Decentralized…

60 min
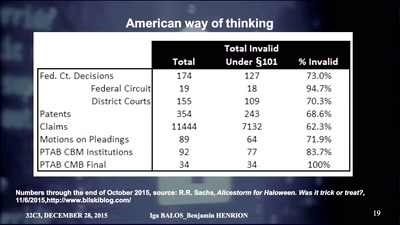
Ein Abgrund von Landesverrat
Wie es dazu kam und was daraus zu lernen ist

61 min
Computational Meta-Psychology
An Artificial Intelligence exploration into the creation of…
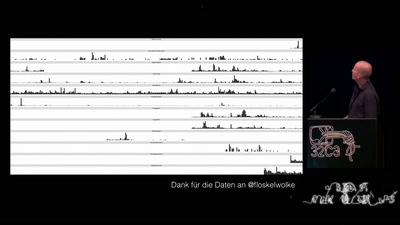
60 min
„Nach bestem Wissen und Gewissen“ – Floskeln in der Politik
Politische Phrasologie – warum man aus dem ganzen Zeug, das…
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

60 min
Shopshifting
The potential for payment system abuse

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

29 min
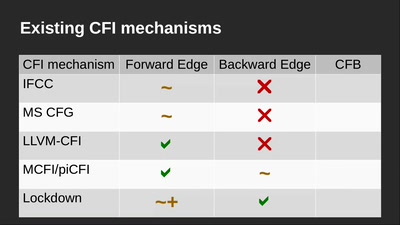
Building and Breaking Wireless Security
Wireless Physical Layer Security & More...

72 min
Console Hacking
Breaking the 3DS
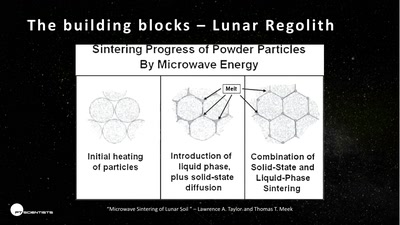
55 min
3D printing on the moon
The future of space exploration

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

60 min
Hardware-Trojaner in Security-Chips
Eine Reise auf die dunkle Seite
60 min
Das Zahnrad aus Fleisch
Expeditionen ins Kommentierreich

60 min
Crypto Wars Part II
The Empires Strike Back

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security
61 min
Avoiding kernel panic: Europe’s biggest fails in digital policy-making
How the institutions fuck up, and how we fuck it up as well
56 min
Iridium Update
more than just pagers
60 min
The Perl Jam 2
The Camel Strikes Back
60 min
Unpatchable
Living with a vulnerable implanted device

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
PLC-Blaster
Ein Computerwurm für PLCs
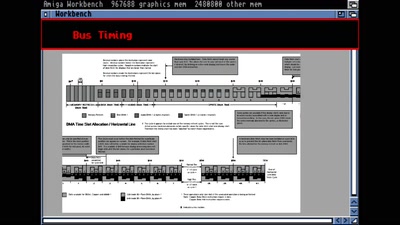
53 min
The Ultimate Amiga 500 Talk
Amiga Hardware Design And Programming
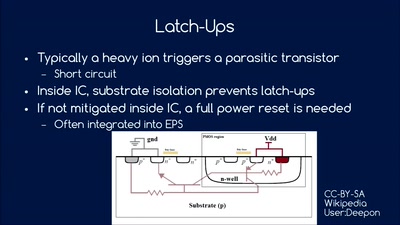
60 min
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development
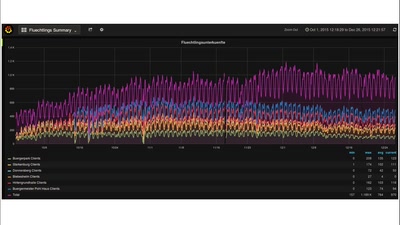
60 min
Lessons learned: Freifunk für Geflüchtete
1 Jahr Freifunk in Südhessen

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…
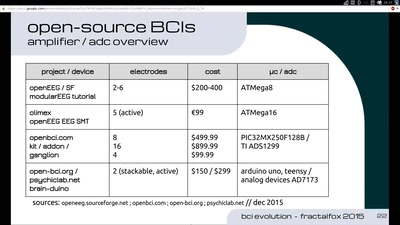
35 min
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

30 min
libusb: Maintainer fail
How I failed to run an open source project
58 min
CHINTERNET ART
Creativity, Archives & Digital Media from the Chinese…

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

30 min
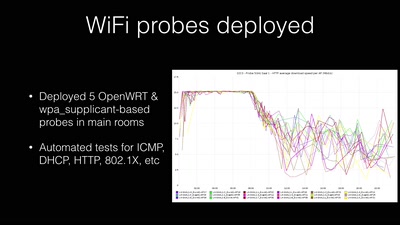
All Our Shared Spectrum Are Belong to Us
Visualizing WLAN Channel Usage on OpenWRT

58 min
When hardware must „just work“
An inside look at x86 CPU design

60 min
Quantum Cryptography
from key distribution to position-based cryptography

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

60 min
Stromtankstellen – eine neue öffentliche Infrastruktur
Was kann das? Wie kann ich das nutzen? Wo besteht…

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…
60 min
G’scheitern
The art of failure taught by improv theatre

61 min
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…
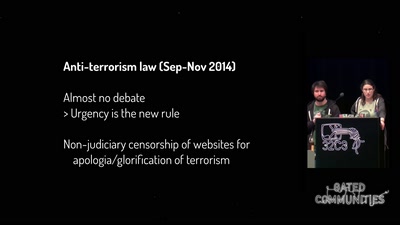
27 min
One year of securitarian drift in France
From the Bill on Intelligence to the State of Emergency

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…

60 min
Buffering sucks!
An attempt of calculating the economic cost of buffering.

59 min
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society
27 min
Maritime Robotics
Hackers, I call thee to our Oceans!

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

61 min
Net Neutrality in Europe
alea iacta est

60 min
Österreich: Der Kampf gegen unkontrollierte Massenüberwachung
Geheimdienste kontrolliert man am besten, indem man ihre…

30 min
apertus° AXIOM
The first Open Source Cinema Camera
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study

61 min
Jugend hackt 2015
Projektvorstellungen der JunghackerInnen

63 min
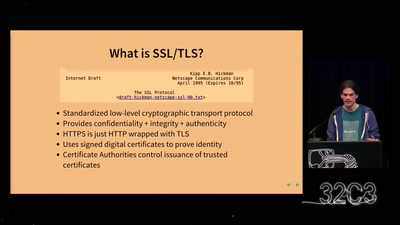
goto fail;
exploring two decades of transport layer insecurity
56 min
Running your own 3G/3.5G network
OpenBSC reloaded

60 min
Internet Cube
Let's Build together a Free, Neutral and Decentralized…
44 min
Replication Prohibited
3D printed key attacks

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…
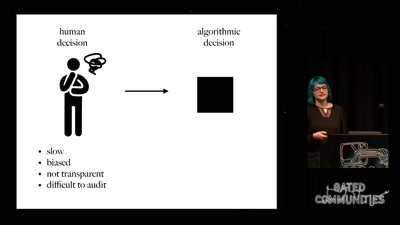
60 min
Prediction and Control
Watching Algorithms

60 min
Windows drivers attack surface
some 'new' insights

53 min
When algorithms fail in our personal lives
Social media break up coordinator

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP

34 min
Ling - High level system programming
modular and precise resource management
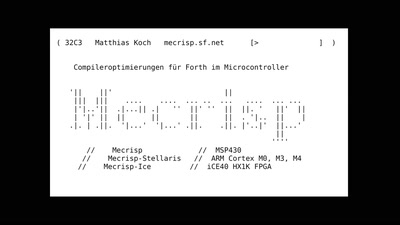
60 min
Compileroptimierungen für Forth im Microcontroller
Mecrisp intern

60 min
Profiling (In)justice
Disaggregating Data by Race and Ethnicity to Curb…
60 min
Netzpolitik in der Schweiz
NDG, BÜPF und wie wir uns dagegen wehren
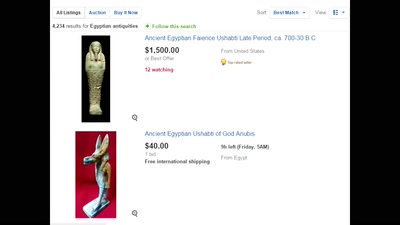
56 min
The mummy unwrapped
Cultural Commons durch Kunstraub

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

32 min
Verified Firewall Ruleset Verification
Math, Functional Programming, Theorem Proving, and an…
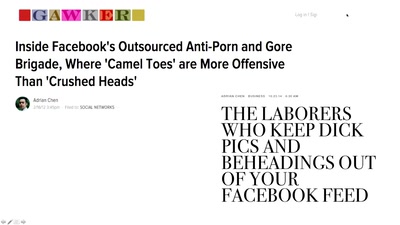
60 min
Sin in the time of Technology
How social media companies are creating a global morality…

22 min
Trust us and our business will expand!
Net-activism strategies against fake web companies

51 min
How to contribute to make open hardware happen
Mooltipass, Openpandora/Pyra and Novena/Senoko: how I…

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

57 min
“I feel like a criminal and I have to be god at the same time”
Perceptions of hackers and hacktivists on their…

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!

30 min
On Computing Numbers, with an Application to Problems of our Society
Journalism ♥ Computer Science

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators
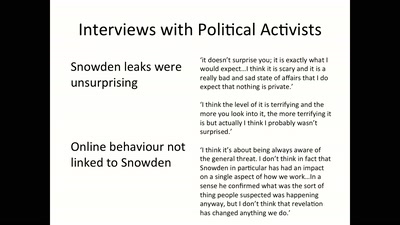
60 min
Media Coverage and the Public in the Surveillance Society
Findings from a Research Project on Digital Surveillance…
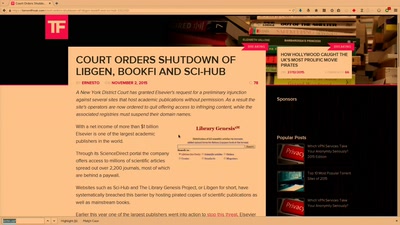
62 min
Public Library/Memory of the World
Access to knowledge for every member of society

32 min