53 min
About military RF communication surveillance and other…

51 min
Secure Boot support in qemu, kvm and ovmf.
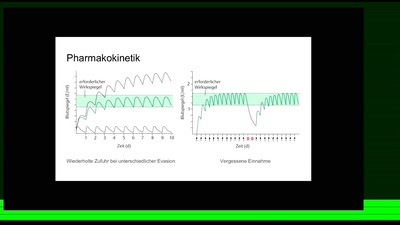
62 min
The usual extremely factual look behind the scenes of this…

60 min
Erinnerungen aus dem virtuellen Ausland in Frankfurt,…
36 min
Theresa May’s effort to abolish privacy

60 min
Was der Anti-Terror-Kampf von der Urheberrechtsdurchsetzung…

33 min
Towards A Global Network Of Neighbourhoods And Cities…
33 min
Deciding between technological utopias in a liberal state

60 min
Schärft das Schwert der Transparenz!

33 min
50 most unwanted retail surveillance technologies / 50 most…

33 min
From Superhuman Sports to Amplifying Human Senses
31 min
Why Censorship is a Bad Idea for Everyone

62 min
Social Life & Life in the early 21st century

113 min
Die Wissenschaftsgala vom 33C3
32 min
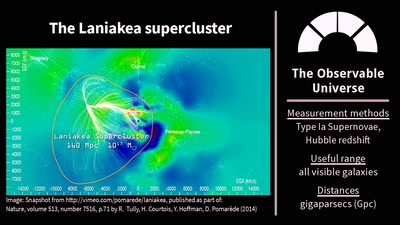
Stuff in Space Is Far Away – but How Do We Know?
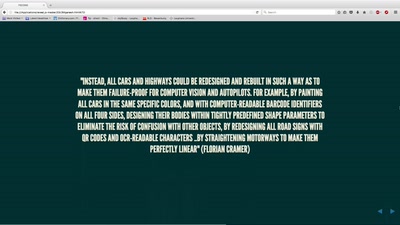
35 min
Power and politics in the development of the driverless car
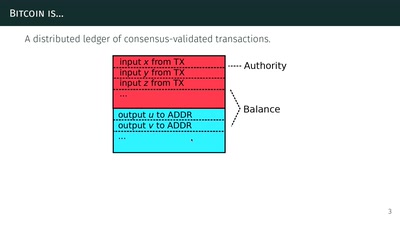
31 min
or zero-knowledge succinct non-interactive arguments of…
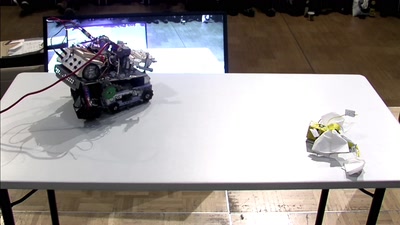
23 min
A sumo style robot battle for intentionally crappy robots!

29 min
An exploration of candy as an engineered material

31 min
an overview of physically unclonable functions

33 min
Dark Matter and Gravitational Waves

29 min
Hackers' knowledge studied by sociologist of science
60 min
10 Jahre Informationsfreiheitsgesetz

33 min
the state at the beginning of the 21st Century

32 min
Refocusing on the moon as a platform for future deep space…
32 min
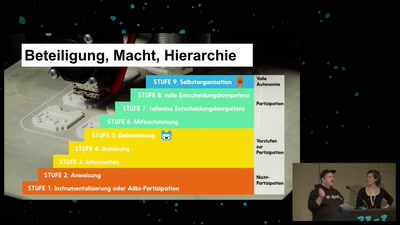
Wie Wertschätzung in (Tech-)Communities gelingen kann
31 min
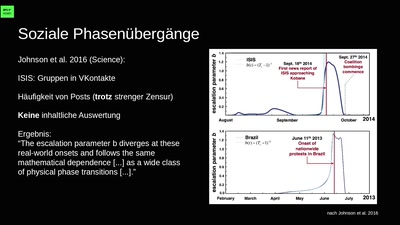
Unsere Daten, die Zukunft und die zerstörte Demokratie

31 min
Hedy Lamarr: Frequency Hopping in Hollywood

53 min
Why Lauri Love’s case is even more important than you…

64 min
Dissecting a Modern Wireless Network for the Internet of…

61 min
Space Transportation and the Extraterrestrial Imperative

63 min
Developing open, FPGA-based capture hardware for conference…
59 min
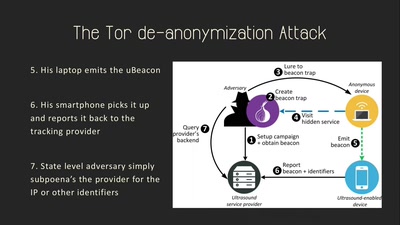
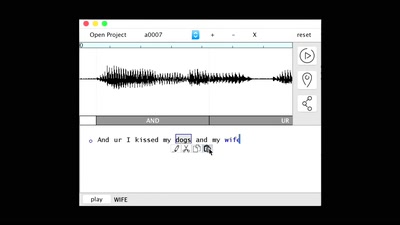
On the Privacy & Security of the Ultrasound Tracking…
57 min
Turbulence, Big Data, AI, Fake News, and Peak Knowledge
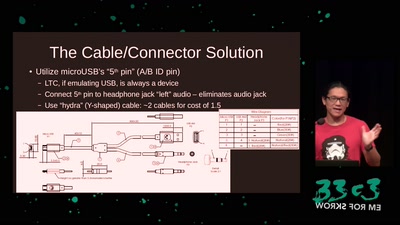
56 min
Introducing the Love to Code Platform

63 min
What you need and how it works. An experiences report

59 min
A tale of 3 different memory deduplication based…

62 min
How thousands of companies are profiling, categorizing,…

53 min
Uncovering Nation-State Mobile Espionage in the Wild
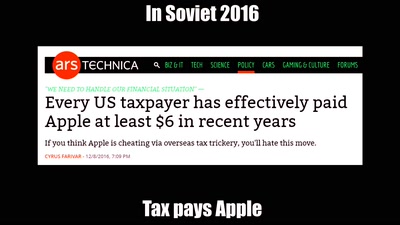
99 min
Wir helfen euch, die Fnords zu sehen!
26 min
Schlagende Argumente, fliegende Fäuste

31 min
A net.art collective since 1995. Understanding the browser…
60 min
…und was wir dagegen tun können
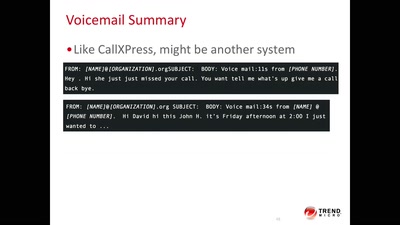
37 min
A systemic update of sensitive information that you sniff…

40 min
Call the frontdoor to install your backdoors

58 min
Wer denkt, Vorratsdatenspeicherungen und „Big Data“ sind…
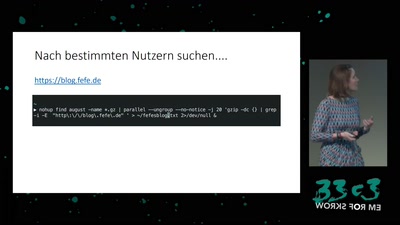
60 min
How private companies leak your personal data into the…

65 min
and How You Can Help the Refugees Who Saved His Life

42 min
How (inter)national money transfers works
64 min
(Not Only) Attacks on OAuth and OpenID Connect
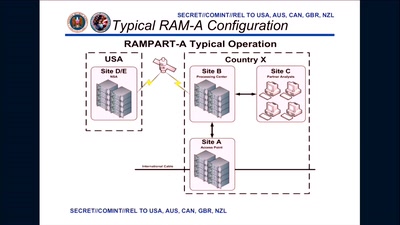
64 min
A Closer Look at the Political Reactions to Mass…

61 min
We must prevent EU copyright reform from breaking the…

60 min
Mixed Reality and multi-sensory communication

57 min
How to write an open source bit-bang low-speed USB stack…

59 min
Wie politische "Gewissheiten" sprachlich konstruiert werden

60 min
Berufe aus vergangenen Zeiten

34 min
Demokratiefeindliches Strafrecht: Die Datenhehlerei gem. §…
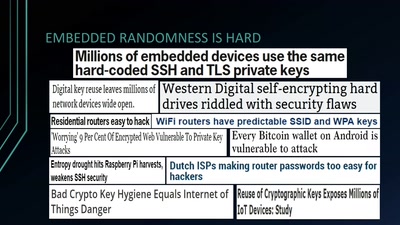
36 min
Analyzing Embedded OS Random Number Generators

33 min
Intrusion and Exfiltration in Server-less Architectures

30 min
IT security is largely a science-free field. This needs to…
28 min
(Did) We Accidentally a New Geological Epoch(?)

26 min
The struggle for security for all.

31 min
The Devolution of Arab Men from Humans to Digital Fodder

30 min
Preserving documentation of human rights violations
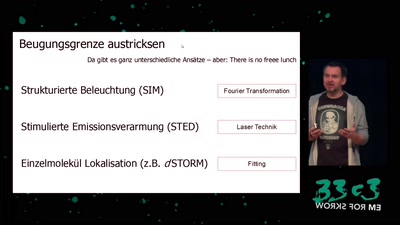
60 min
von Mikroskopen, Wahrnehmung und warum das kaum jemanden…
26 min
Technology and Politics in Congress Talks, from 1984 to now

63 min
A gentle introduction to mobile messaging and subsequent…

65 min
Ein Geheimdienst als Zeuge. Szenen aus dem…

59 min
A Journey in the Land of (Cyber-)Espionage

46 min
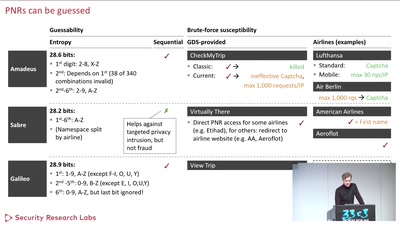
Finding interesting targets in 128bit of entropy
61 min
Ein Jahresrückblick aus dem Land der Datenberge

60 min
...or why adding BTLE to a device sometimes isn't smart at…
59 min
Becoming a secret travel agent

61 min
Improving the encrypted the web, one round-trip at a time

62 min
Grundrechte per Volksentscheid versenken
60 min
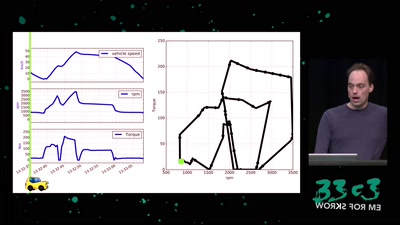
A hacker’s review of Dieselgate

57 min
Eine kleine Einführung in den 802.11ac Standard
25 min
Type In Beyond the Scrolling Horizon

34 min
Wie mit Gerüchten über Geflüchtete im Netz Stimmung gemacht…

32 min
The Role of Automation Dependency in Aviation Accidents

61 min
A proposal for secure computing in an age where we cannot…

32 min
How cold data can make you feel things.
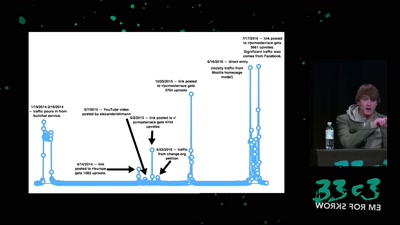
31 min
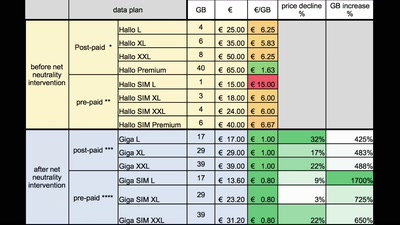
Let's put the new EU Net Neutrality rules to work

60 min
Was Aktivisten davon lernen können

29 min
Technical Teardown of the Pegasus malware and Trident…

60 min
Prejudice in Word Embeddings

33 min
Wider die automatisierte Rechtsdurchsetzung

30 min
The Red Pill of N26 Security
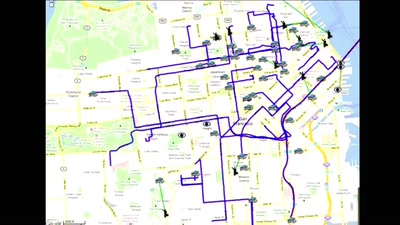
33 min
How mapping creates space, shapes cities and our view of…

31 min
How the FBI and local cops are hacking computers outside of…
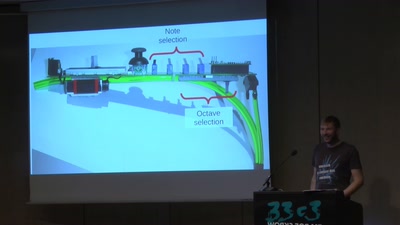
20 min
A DIY MIDI Controller and a New UI for Wind Instruments

60 min
Polizeiliche Datenbanken und was man über seinen Auskunfts-…

60 min
Crypto fight in the Wake of Apple v. FBI

60 min
Lessons learnt implementing PCIe on FPGA for XTRX Software…

44 min
teaching a new dog old tricks

55 min
Side effects include side-channel attacks and bypassing…

63 min
The Infrastructure and People behind Drone Killings