Events for tag "30c3"

29 min
2 Takte später
30C3S SCE mbH: GEMA-Konkurrenz für Fortgeschrittene
45 min
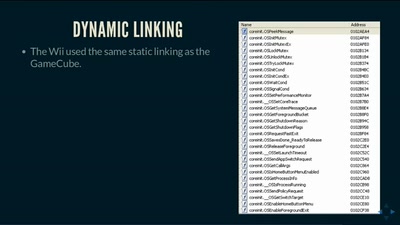
HbbTV Security
OMG - my Smart TV got pr0wn3d

60 min
30C3 Opening Event
Welcome to the 30th Chaos Communication Congress

42 min
Das FlipDot-Projekt
Spaß mit mechanischer Anzeige

26 min
Technomonopolies
How technology is used to subvert and circumvent…

36 min
Sim Gishel
A singing and dancing robot build to take part in casting…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
57 min
Hello World!
How to make art after Snowden?

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

29 min
Perfect Paul
On Freedom of Facial Expression

58 min
07KINGSTON25 JAMAICA: MALARIA UPDATE Dispatches from Fort Meade
Reporting on the secret trial of Chelsea Manning

30 min
The ArduGuitar
An Arduino Powered Electric Guitar

24 min
The Four Wars
Terror, whistleblowers, drugs, internet

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

45 min
To Protect And Infect
The militarization of the Internet

71 min
30C3 Infrastructure Review
Presentation of MOC/NOC/VOC/SOC/*OC

60 min
Concepts for global TSCM
getting out of surveillance state mode

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

55 min
White-Box Cryptography
Survey

29 min
lasers in space
more than just pew pew!

58 min
Überwachen und Sprache
How to do things with words
41 min
SCADA StrangeLove 2
We already know

66 min
Die Drohnenkriege
Kriegsführung der Zukunft?

61 min
Dead Man Edition
Auf dem Weg zu fairer Elektronik am Beispiel der Elkos …

147 min
Hacker Jeopardy
Zahlenraten für Geeks [Number guessing for geeks]
60 min
Desperately Seeking Susy
A farewell to a bold proposal?

64 min
Magic Lantern
Free Software on Your Camera
48 min
10 Years of Fun with Embedded Devices
How OpenWrt evolved from a WRT54G firmware to an universal…
61 min
X Security
It's worse than it looks

29 min
The Pirate Cinema
Creating mash-up movies by hidden activity and geography of…

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows
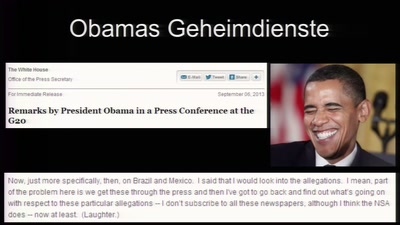
117 min
Fnord News Show
Der schonungslose Realitätsabgleich mit…
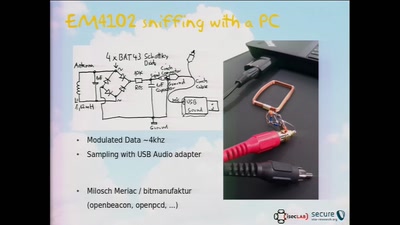
58 min
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems
26 min
Against Metadata
Twisting time and space to explore the unknown

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

59 min
Zwischen supersicherer Verschlüsselung und Klartext liegt nur ein falsches Bit
Ein Streifzug durch die Fehler in der Kryptografie
31 min
Nerds in the news
Spending a year coding in a newsroom

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice

58 min
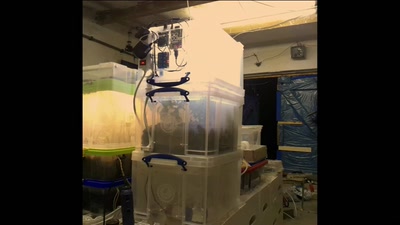
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
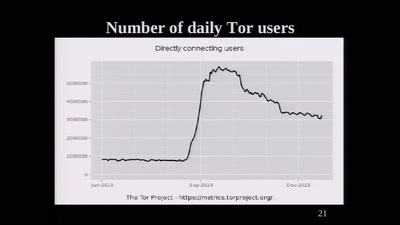
62 min
The Tor Network
We're living in interesting times

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…
58 min
Script Your Car!
Using existing hardware platforms to integrate python into…
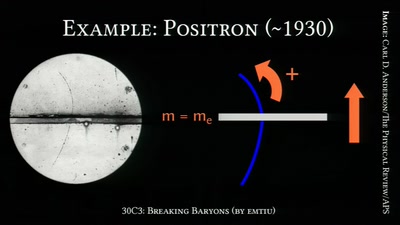
60 min
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders
32 min
Human Rights and Technology
"A New Hope" or "The Empire Strikes Back"?

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

64 min
We only have one earth
A case for expansionistic space policy

33 min
Hacking as Artistic Practice
!Mediengruppe Bitnik about their recent works
47 min
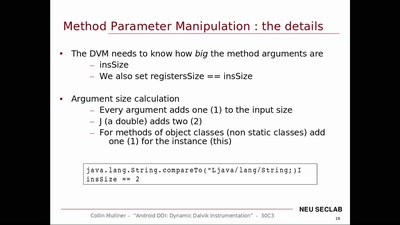
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…
30 min
The philosophy of hacking
Contemplations on the essence of hacking and its…

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…
46 min
Basics of Digital Wireless Communication
introduction to software radio principles
56 min
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache
36 min
Long Distance Quantum Communication
Concepts and components for intercontinal communication…
60 min
Bullshit made in Germany
So hosten Sie Ihre De-Mail, E-Mail und Cloud direkt beim…

33 min
Open source experimental incubator build up
call for participation in project and product development

59 min
Security of the IC Backside
The future of IC analysis

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

56 min
WarGames in memory
what is the winning move?
47 min
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish

48 min
Seidenstraße
The Making of…

33 min
Turing Complete User
What can be done to protect the term, the notion and the…

58 min
Baseband Exploitation in 2013
Hexagon challenges

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

90 min
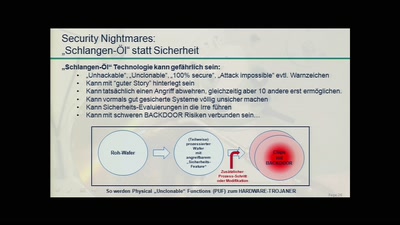
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…

61 min
Warum die Digitale Revolution des Lernens gescheitert ist.
Fünf Desillusionen
56 min
Electronic Bank Robberies
Stealing Money from ATMs with Malware
61 min
25 Jahre Chipkarten-Angriffe
Von der Historie zur Zukunft
54 min
Der Kampf um Netzneutralität
Wer kontrolliert das Netz?
38 min
Policing the Romantic Crowd
Velocipedes and Face Recognition

46 min
CounterStrike
Lawful Interception
26 min
Plants & Machines
Food replicating Robots from Open Source Technologies

55 min
How to Build a Mind
Artificial Intelligence Reloaded

61 min
Programming FPGAs with PSHDL
Let's create the Arduino for FPGAs
46 min
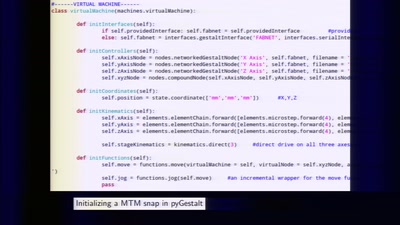
Making machines that make
rapid prototyping of digital fabrication and…
33 min
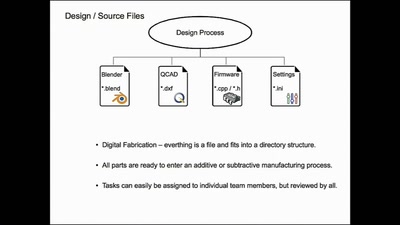
Structuring open hardware projects
experiences from the “i3 Berlin” 3D printer project with…

39 min
Hacking the Czech Parliament via SMS
A parliamentary drama of 223 actors

62 min
To Protect And Infect, Part 2
The militarization of the Internet
32 min
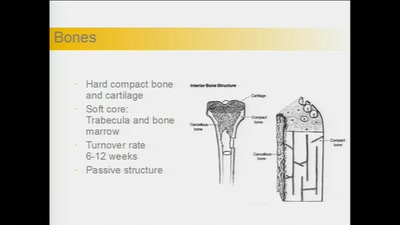
Coding your body
How to decipher the messages of your body

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

63 min
Through a PRISM, Darkly
Everything we know about NSA spying

66 min
Keine Anhaltspunkte für flächendeckende Überwachung
Die Diskussion um NSA, PRISM, Tempora sprachlich und…

51 min
The GNU Name System
A Decentralized PKI For Social Movements

54 min
Do You Think That's Funny?
Art Practice under the Regime of Anti-Terror Legislation

65 min
Mind-Hacking mit Psychedelika
Eine Einführung in die Wirkungsweise psychedelischer…

31 min