16 min
How To Make Human Machine Readable

19 min
Investigating the dark side of meaning production
20 min
(let's hack OUTER space, the final frontier)

21 min
Computer haben Gefühle, wir helfen ihnen, sie auszudrücken

22 min
Fighting code-abuse by military and intelligence

24 min
Nothing shows pride like letting others destroy what you’ve…
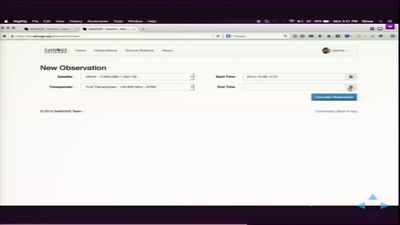
25 min
open source ground station, optimized for modularity, built…
![for women in "${tech[@]}"; do](https://static.media.ccc.de/media/conferences/camp2015/6774-hd.jpg)
26 min
Let's talk, share and learn from each other.

26 min
The right to be counted, or the right to be left alone?

27 min
Wait what? Why not digital?

27 min
fermenting together for better future

28 min
Creating a usable tool against online trackers
28 min
How to retrieve secret keys without going bankrupt

28 min
Bots are waging a dirty war in Mexican social media.

29 min
How to freely share research without being arrested

29 min
A need to know on soilless growing before building,…

30 min
Stop being tracked online

30 min
Die Bundesregierung will offene WLANs verhindern, aber das…
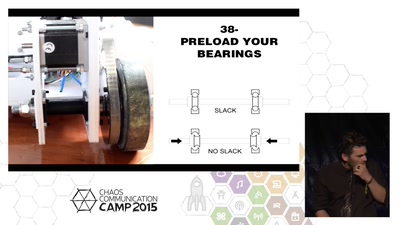
30 min
A rather unstructured selection of things I wished I knew…

30 min
Our experiences of building and running Tor servers
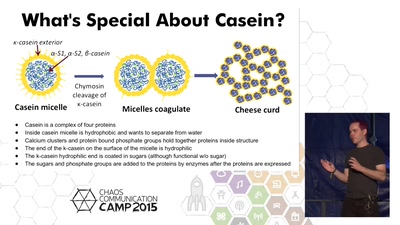
30 min
Engineering yeast to produce casein

30 min
Questioning privacy, data protection, and autonomy in the…

31 min
Eine Such-Reportage nach der physischen Seite des Netz
31 min
Opensource and Venture Capital, Softwaredevelopment and…

31 min
More frequency spectrum with better propagation properties…

32 min
Wie eine investigative Recherche zum geheimen Ausbau der…

34 min
Evolution and design of new interfaces for musical…

36 min
A creative drink for the commons

40 min
A To Do list for Cyptographic Research and Implementations
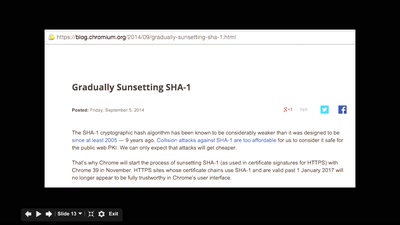
42 min
A Certificate Authority To Encrypt the Entire Web

45 min
Personal production of bio-fuels
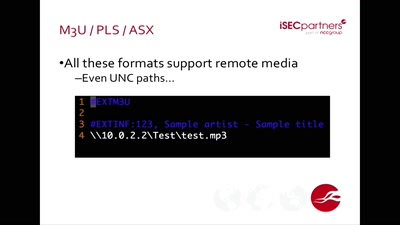
46 min
Is Your Document Telling on You?
47 min
Integrating FPGAs with standard personal computers

48 min
Making medical devices accessible and hackable for all
48 min
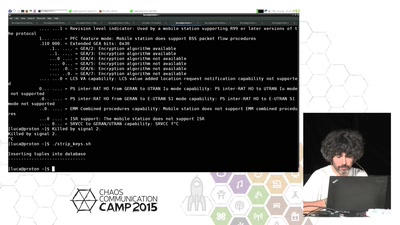
Chasing GRX and SS7 vulns

51 min
Neue Perspektiven und Ideen für zivilen Ungehorsam
52 min
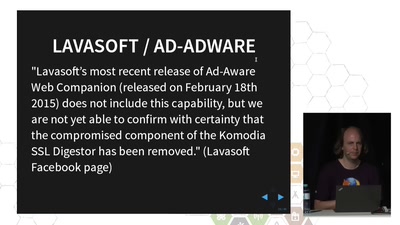
How Man-in-the-Middle filtering solutions harm the security…

54 min
Die Wahrheit™ über den Absturz - eine Transparenzoffensive

54 min
A Practical Introduction to Acoustic Cryptanalysis

54 min
Anhörung zur verdeckten Infiltration von IT-Systemen
55 min
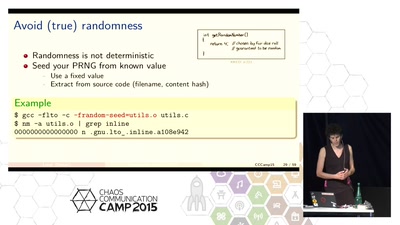
Get a verifiable path from source to binary

55 min
Failures, Challenges, and the Future

56 min
Zwischen den geschwärzten Zeilen lesen
56 min
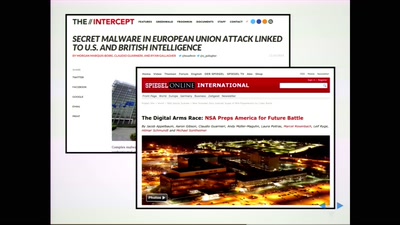
Targeted threats to civil society

58 min
Practical terraforming technologies for regenerating soils…

58 min
Keeping it short & simple. Oder: Wozu man Hunde mit…
58 min
How did GCHQ do it to the Guardian's copy of Snowden's…
59 min
Bridging the gap between DIY and professional electronics

59 min
Nifty technologies behind the world's most sensitive…
60 min
The infiltration and physical surveillance of social…
60 min
Let's do everything except the pots by ourselves

60 min
Experiences with the open source laser cutter

60 min
„Der Profi macht nur neue Fehler. Der Dummkopf wiederholt…

63 min
Funding open source with money from corporations and…

63 min
Bringing Internet access to those who need it most.
69 min
The State of the Hack in India. A place to be^W hack in the…







![for women in "${tech[@]}"; do](https://static.media.ccc.de/media/conferences/camp2015/6774-hd.jpg)