Search for "851" returned 1867 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

62 min
HUMUS sapiens
Open Soil Research

62 min
Transhuman Expression
Interdisciplinary research in Painting and Robotics. with…

62 min
To Protect And Infect, Part 2
The militarization of the Internet

59 min
Provable Security
How I learned to stop worrying and love the backdoor

57 min
Theater und Quantenzeitalter
„Die Parallelwelt“- Das Schauspiel Dortmund und die…

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…
61 min
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications

65 min
The Untold Story of Edward Snowden’s Escape from Hong Kong
and How You Can Help the Refugees Who Saved His Life

58 min
PLC-Blaster
Ein Computerwurm für PLCs
47 min
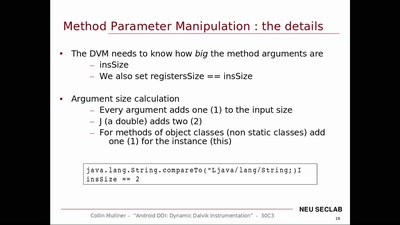
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…

72 min
Console Hacking
Breaking the 3DS

27 min
Chaos Zone
Chaos Family

61 min