Search for "11" returned 4574 results

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

54 min
A la recherche de l'information perdue
some technofeminist reflections on Wikileaks

55 min
3D Casting Aluminum
Too Much Fun with Microwaves

60 min
Lets break modern binary code obfuscation
A semantics based approach

43 min
This is NOT a proposal about mass surveillance!
Analysing the terminology of the UK’s Snooper’s Charter

30 min
apertus° AXIOM
The first Open Source Cinema Camera

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation
31 min
Trackography
You never read alone

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine
60 min
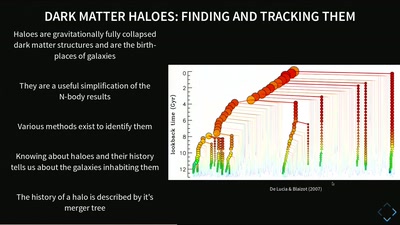
Simulating Universes
What Virtual Universes Can Tell Us About Our Own

30 min
0en & 1en auf dem Acker
Was die Sensor & Automatisierungstechnik in der…
62 min
Internet, the Business Side
a try to explain the ecosystem

64 min