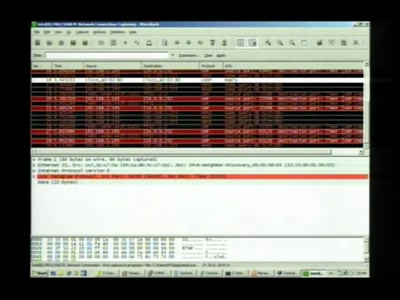
28 min
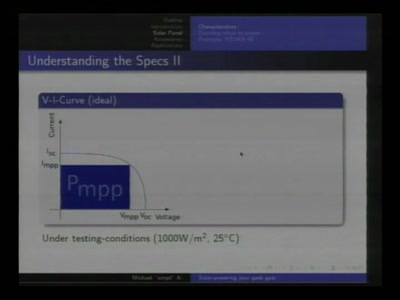
Alternative and mobile power for all your little toys
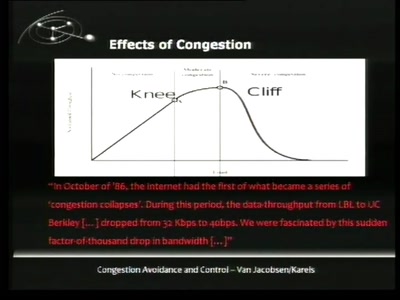
30 min
Accepting the Partial Disclosure Challenge
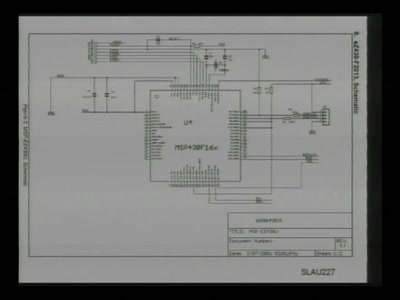
33 min
with msp430static, solder, and syringe
35 min
A clever or ingenious device or expedient; adroit…

38 min
How to get useable information out of your honeypot

39 min
Formica: a cheap, open research platform

44 min
Building an anonymous Internet within the Internet

44 min
If technology is the solution, politicians are the problem

44 min
Global-scale Incident Response and Responders

44 min
State of the Art in Wearable Computing

45 min
Social networks based on XMPP
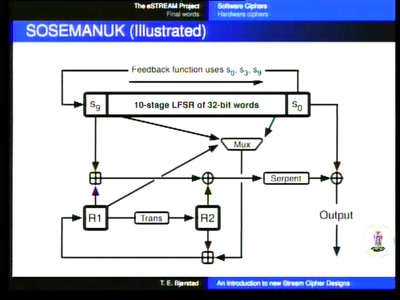
46 min
Turning data into line noise and back

47 min
Ein audiovisuelles Live-Feature

48 min
The silent march of the multinational GMO soy industry and…

48 min
Enhancing the value of privacy in todays students view

48 min
Hide and Seek in A. Flash

48 min
Reverse Engineering von 3D-Dateiformaten

49 min
Developing rules for autonomous systems
49 min
The Hackerspace's Junior Academy
50 min
PowerLineCommunications has now their open source tool

50 min
Wir helfen Euch, die Fnords zu sehen

50 min
We help in seeing teh Fnords

50 min
Open source BIOS replacement with a radical approach to…

51 min
Doing music with microcontrollers

51 min
Ein Idylle aus der Analogsteinzeit der Überwachung

52 min
How RepRap and physical compilers will change the world as…

52 min
Forderungen nach dem Jahr der Datenverbrechen

55 min
Festplattenbeschlagnahme in neuem Licht
55 min
Dawn of the high-throughput DNA sequencing era

56 min
Is implementation the enemy of design?
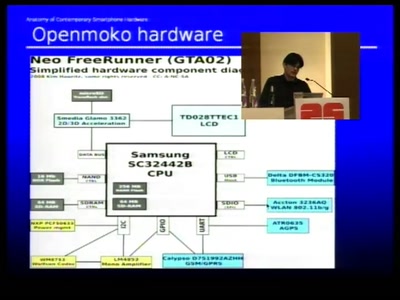
56 min
Dissecting contemporary cellphone hardware

57 min
The time is now to make anything you can imagine
57 min
Rückblick über eine bewegte Zeit
58 min
Pwning Apple's Mobile Internet Device

58 min
More security-critical behaviour in Europe!
58 min
Recovering keys and other secrets after power off

58 min
Storage and Access of Pornographic Information

58 min
Tampering the Tamper-Proof

59 min
Optimism towards a future where there is "Nothing to hide"
60 min
Exploiting the weather with unpowered aircraft

60 min
Why the idea of data protection slowly turns out to be…

60 min
Endlich wird jeder zum "Trusted Citizen"
61 min
Everything about the C64 in 64 Minutes

61 min
Bestandsaufnahme und Auswirkungen

61 min
Essentielles Grundwissen für alle, die nichts zu verbergen…

61 min
Not your mother's XSS bugs

61 min
Creating a rogue CA Certificate

62 min
Past, present, and future
63 min
Symbian Exploit and Shellcode Development
63 min
Overview of Current Keylogger Threats

65 min
Behind the scenes of the new light installation
65 min
Why cryptography might not fix the issue of transparent…

65 min
Some cases of terrorism around the world that are not…

65 min
What we did so far. What will happen in the future.

66 min
Pan-european activism for patching a "pirated" law
66 min
The Digital Enhanced Cordless Telecommunications standard
67 min
An overview of holographic techniques

70 min
Politikersprache zwischen Orwell und Online

76 min
Breaking Remote Keyless Entry Systems with Power Analysis

82 min
First look at the security of NFC mobile phones

92 min
Or: about what we will laugh next year
94 min
Oder: worüber wir nächstes Jahr lachen werden

102 min
The ultimative Hacker-Quizshow

103 min
Die ultimative Hacker-Quizshow

125 min
Die Themen des CCC im Jahr 2008