Search for ".yof" returned 7511 results
38 min
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices
52 min
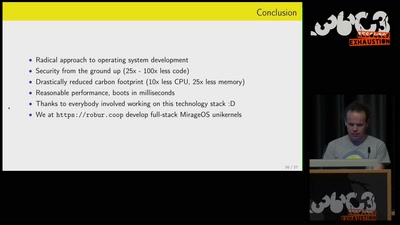
Leaving legacy behind
Reducing carbon footprint of network services with MirageOS…

81 min
Energy Harvesting for Smart Autonomous Electronics 2
Towards a future of autonomous wireless electronics without…
62 min
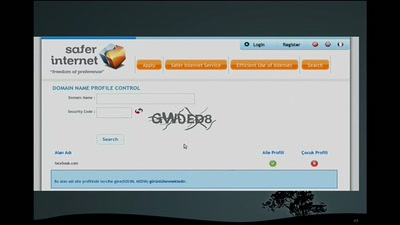
The movements against state-controlled Internet in Turkey
A short account of its history and future challenges
61 min
Hacking the universe
When strings are super and not made of characters
44 min
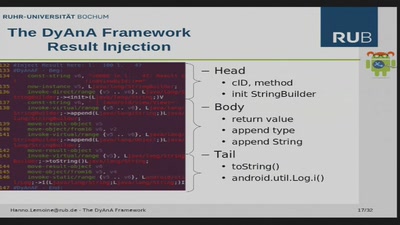
Dynamic Malware Analysis on Android Phones
Presentation of the DyAnA Framework (Dynamic Android…
63 min
Hacking German Elections
Insecure Electronic Vote Counting - How It Returned and Why…
35 min
Remote Attestation in MicroOS
Measuring the health of our system with a TPM
43 min
The Mars Rover On-board Computer
How Curiosity's Onboard Computer works, and what you can…

19 min
Delta Chat messenger
unlocking the potential of e-mail and the web
41 min
Introduction to (home) network security.
A beginner-friendly guide to network segmentation for…
47 min
Distributed Actor System with Rust
Learn about the building blocks of a network application
31 min
Working together in one place with Nextcloud
What's scaring Big Tech today
59 min
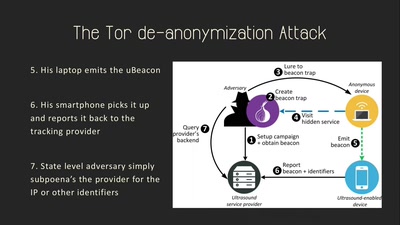
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…
42 min
Terminator Genes and GURT - Biological Restrictions Management
Five Years after the announcement of a quasi moratorium

59 min
10GE monitoring live!
How to find that special one out of millions

52 min
Adventures in Mapping Afghanistan Elections
The story of 3 Ushahidi mapping and reporting projects.

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety
53 min
Crouching Powerpoint, Hidden Trojan
An analysis of targeted attacks from 2005 to 2007

48 min
The Privacy Workshop Project
Enhancing the value of privacy in todays students view

53 min