Search for "Lisa" returned 984 results
113 min
Das Bits&Bäume-Sporangium
8 Mikrokosmen, 8 Expert*innen, je 8 Minuten zu…
35 min
Access to Tools (in Graphic design)
Werkzeuge für Typografie, Grafikdesign und einen…

62 min
Post Memory Corruption Memory Analysis
Automating exploitation of invalid memory writes

47 min
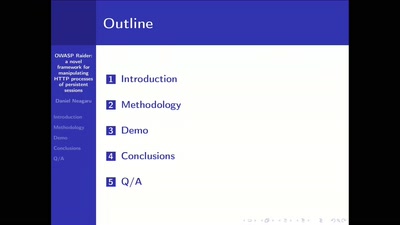
OWASP Raider
a novel framework for manipulating HTTP processes of…
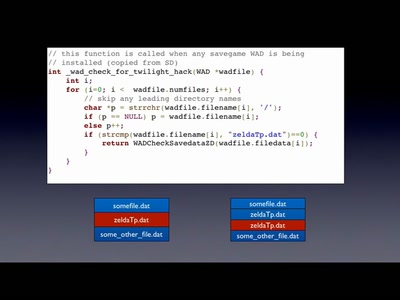
46 min
Embedded device security nightmares
An Introduction to the usual mistakes

39 min
PrivacyScore.org
Test websites and rank them according to their security and…
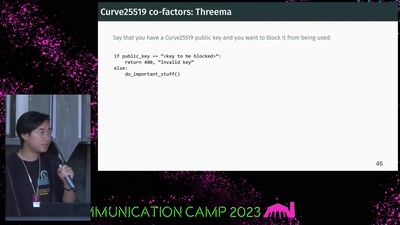
43 min