Search for "357" returned 1992 results

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…

68 min
#afdwegbassen: Protest, (Club-)Kultur und antifaschistischer Widerstand
Über kreative Organisation, poltische Aktionen und das…
60 min
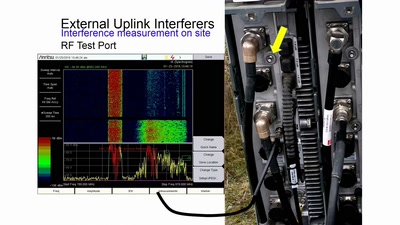
Die verborgene Seite des Mobilfunks
HF-Störquellen im Uplink

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge
58 min
CHINTERNET ART
Creativity, Archives & Digital Media from the Chinese…

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…

61 min
Quantenphysik und Kosmologie
Eine Einführung für blutige Anfänger

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…

67 min