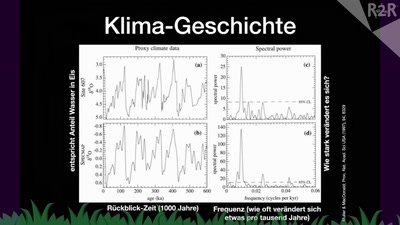
Search for "16" returned 4652 results

30 min
apertus° AXIOM
The first Open Source Cinema Camera

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…
41 min
Archäologische Studien im Datenmüll
Welche Daten speichert Amazon über uns?

36 min
Modchips of the State
Hardware implants in the supply-chain

30 min
0en & 1en auf dem Acker
Was die Sensor & Automatisierungstechnik in der…

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine
31 min
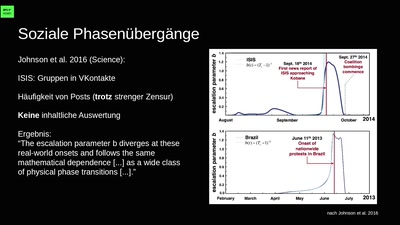
Berechnete Welt
Unsere Daten, die Zukunft und die zerstörte Demokratie

31 min
BGP and the Rule of Custom
How the internet self-governs without international law

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…
32 min
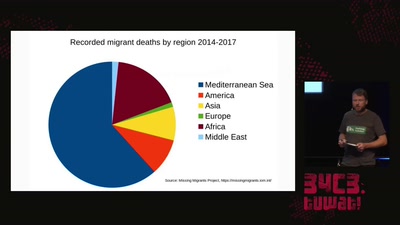
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized

60 min
Hardware-Trojaner in Security-Chips
Eine Reise auf die dunkle Seite
60 min