Search for "17" returned 4551 results

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting
60 min
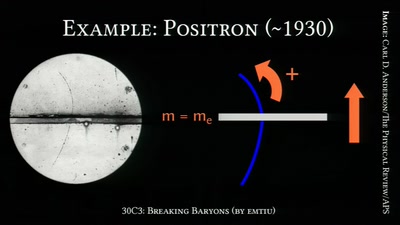
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

60 min
Shopshifting
The potential for payment system abuse
56 min
Rhetorische Selbstsabotage: Was eigentlich passiert, wenn wir reden
Einige Gedanken über Stimme und wie wir sagen können, was…

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…
63 min
Kritikalität von Rohstoffen - wann platzt die Bombe?
Ein nicht nuklearer Blick auf das Ende der Welt

53 min
From Maxwell to antenna arrays
How 150 year old equations still help to communicate
54 min
How medicine discovered sex
Introduction to sex- and gender-sensitive medicine
36 min
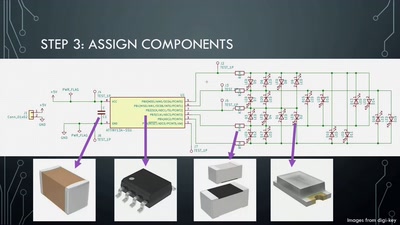
Artistic PCB Design and Fabrication
From doodle to manufacture: how I make mechanically…

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

43 min
How Facebook tracks you on Android
(even if you don’t have a Facebook account)

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

61 min
Programming FPGAs with PSHDL
Let's create the Arduino for FPGAs

49 min