Search for "25" returned 4422 results

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)
35 min
Wallet Security
How (not) to protect private keys

34 min
Social Cooling - big data’s unintended side effect
How the reputation economy is creating data-driven…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

54 min
World War II Hackers
Stalin's best men, armed with paper and pen
32 min
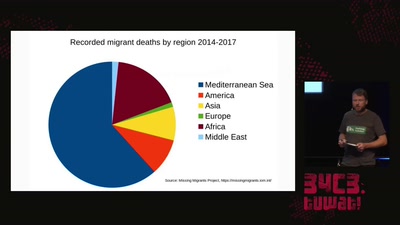
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon

26 min
Opening Event
35C3: Refreshing Memories

58 min
Überwachen und Sprache
How to do things with words

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

42 min