Search for "10" returned 5085 results

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

28 min
Long war tactics
or how we learned to stop worrying and love the NSA
60 min
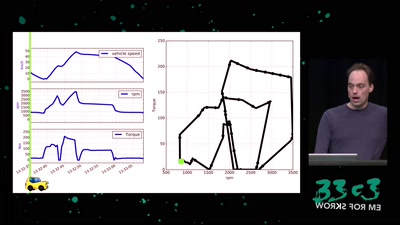
Software Defined Emissions
A hacker’s review of Dieselgate

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy
52 min
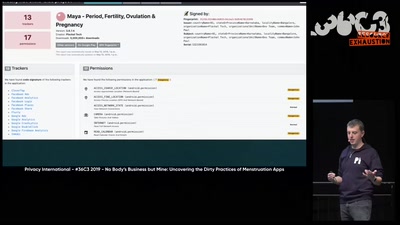
No Body's Business But Mine, a dive into Menstruation Apps
The Not-So Secret Data Sharing Practices Of Menstruation…
20 min
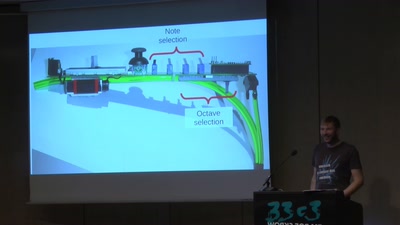
The Nibbletronic
A DIY MIDI Controller and a New UI for Wind Instruments
64 min
Hacking the Media: Geflüchtete schmuggeln, Nazis torten, Pässe fälschen
Warum wir zivilen Ungehorsam und Subversion mehr brauchen…

46 min
CounterStrike
Lawful Interception

30 min
The ArduGuitar
An Arduino Powered Electric Guitar
61 min
Trügerische Sicherheit
Wie die Überwachung unsere Sicherheit gefährdet

67 min
Freude ist nur ein Mangel an Information
Ein Demotivationsworkshop zur politischen Lage.

41 min
Wandel im Braunkohlerevier: Lithium-Ionen-Batterierecycling
Eine industrielle Perspektive für die Lausitz?

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon
31 min