Search for "148" returned 2388 results

26 min
Technomonopolies
How technology is used to subvert and circumvent…

62 min
To Protect And Infect, Part 2
The militarization of the Internet

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.
60 min
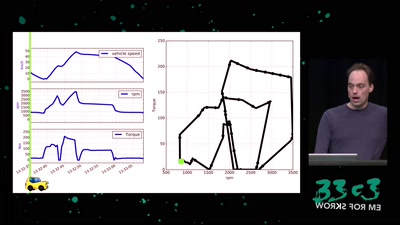
Software Defined Emissions
A hacker’s review of Dieselgate

60 min
Lets break modern binary code obfuscation
A semantics based approach

62 min
radare demystified
after 1.0

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

46 min
CounterStrike
Lawful Interception

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics
52 min
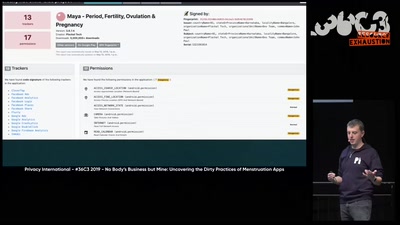
No Body's Business But Mine, a dive into Menstruation Apps
The Not-So Secret Data Sharing Practices Of Menstruation…

63 min