Search for "535" returned 2045 results

58 min
When hardware must „just work“
An inside look at x86 CPU design

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

62 min
To Protect And Infect, Part 2
The militarization of the Internet

60 min
Concepts for global TSCM
getting out of surveillance state mode

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

53 min
Console Hacking 2016
PS4: PC Master Race

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…
60 min
Theresa Hannig – Fireside Chat
Lesung und Hintergrundgespräch

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

62 min
Space Ops 101
An introduction to Spacecraft Operations

31 min
Demystifying Network Cards
Things you always wanted to know about NIC drivers

50 min
The eXperimental Robot Project
An open-hardware bipedal walking machine
60 min
Software Defined Emissions
A hacker’s review of Dieselgate
60 min
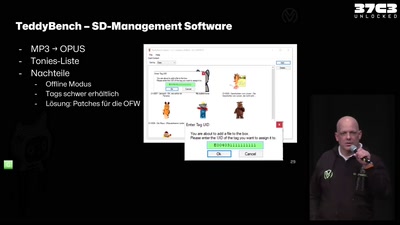
Toniebox Reverse Engineering
Eine Musikbox für Kinder, Maker und Hacker

61 min