Search for "366" returned 1945 results
60 min
Die verborgene Seite des Mobilfunks
HF-Störquellen im Uplink

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge
58 min
CHINTERNET ART
Creativity, Archives & Digital Media from the Chinese…

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…

61 min
Quantenphysik und Kosmologie
Eine Einführung für blutige Anfänger

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…

67 min
The Maker movement meets patent law
How many windows are open in the patent fortress

60 min
Mein Bot, der Kombattant
Operative Kommunikation im digitalen Informationskrieg
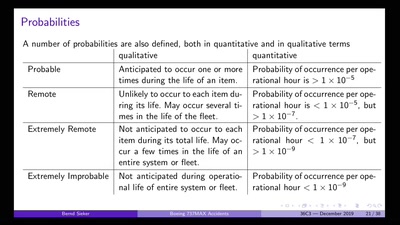
60 min
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system
42 min
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…
38 min
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices

60 min