Search for "428" returned 2020 results

64 min
ES GIBT VIEL ZU TUN - HAU'N WIR AB.
[Die Untersuchung]

46 min
Remo2hbo -Robustes und reparierbares Vitalparametermonitoring
Medizingeräte für Alle
44 min
Replication Prohibited
3D printed key attacks
48 min
10 Years of Fun with Embedded Devices
How OpenWrt evolved from a WRT54G firmware to an universal…

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux

60 min
Crypto Wars Part II
The Empires Strike Back

62 min
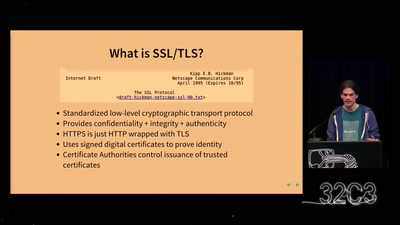
Let's Encrypt
A Free Robotic Certificate Authority

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption
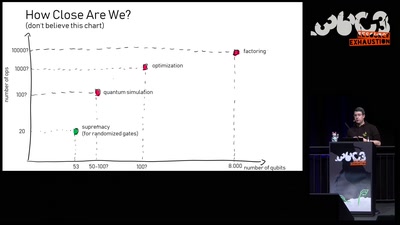
61 min
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley
62 min