Search for "id4=WH0n" returned 328 results

58 min
When hardware must „just work“
An inside look at x86 CPU design
61 min
Holography of Wi-Fi radiation
Can we see the stray radiation of wireless devices? And…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

59 min
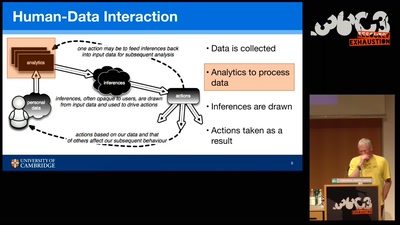
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society

31 min
Extended DNA Analysis
Political pressure for DNA-based facial composites

58 min
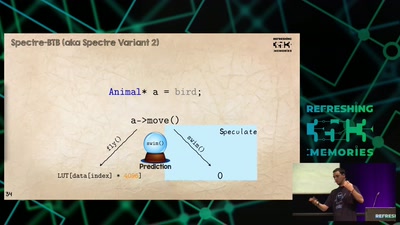
Baseband Exploitation in 2013
Hexagon challenges
61 min
Rocket Kitten: Advanced Off-the-Shelf Targeted Attacks Against Nation States
A Deep Technical Analysis

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows

53 min
Million Dollar Dissidents and the Rest of Us
Uncovering Nation-State Mobile Espionage in the Wild
58 min
The Internet in Cuba: A Story of Community Resilience
Get a unique tour of some of the world’s most unusual…

61 min