Search for "15" returned 4923 results

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people
60 min
Freedom needs fighters!
Wie die GFF mit strategischen Klagen für Freiheitsrechte…

33 min
Antipatterns und Missverständnisse in der Softwareentwicklung
Eine Geschichte voller Missverständnisse

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

55 min
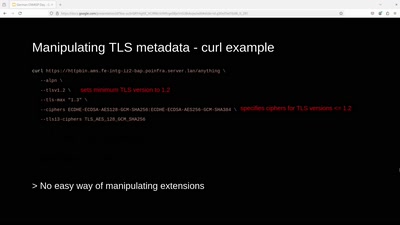
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks
61 min
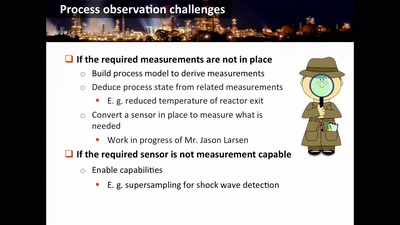
Damn Vulnerable Chemical Process
Exploitation in a new media

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…

95 min
The Time is Right
Ein Science-Fiction-Theaterstück

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs
56 min
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

55 min