Search for "12" returned 5164 results

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

62 min
Was schützt eigentlich der Datenschutz?
Warum DatenschützerInnen aufhören müssen von individueller…
48 min
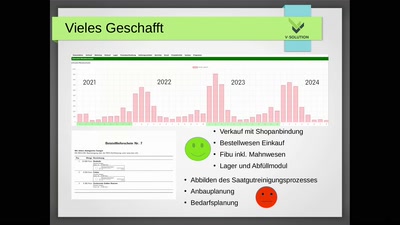
kivitendo - OpenSource ERP für den Saatgutanbau
Vom Acker - In die Welt
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!

58 min
Open Source Estrogen
From molecular colonization to molecular collaboration

65 min
Mind-Hacking mit Psychedelika
Eine Einführung in die Wirkungsweise psychedelischer…

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting
60 min
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders

60 min
Shopshifting
The potential for payment system abuse

55 min
The DROWN Attack
Breaking TLS using SSLv2
60 min
Desperately Seeking Susy
A farewell to a bold proposal?

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

47 min
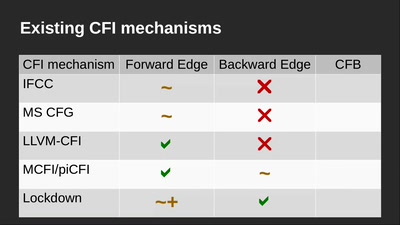
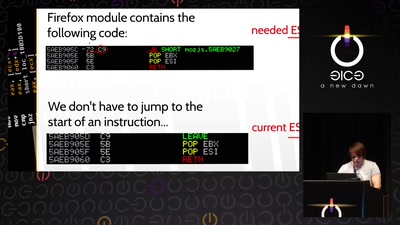
Bug class genocide
Applying science to eliminate 100% of buffer overflows
62 min
The Tor Network
We're living in interesting times
63 min
Kritikalität von Rohstoffen - wann platzt die Bombe?
Ein nicht nuklearer Blick auf das Ende der Welt

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…

60 min