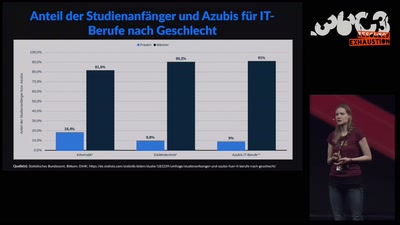
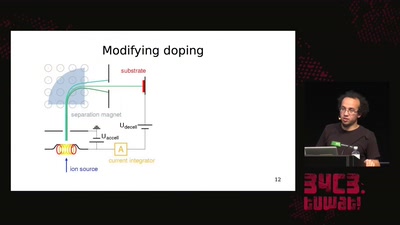
Search for "18" returned 4659 results

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

34 min
Social Cooling - big data’s unintended side effect
How the reputation economy is creating data-driven…

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.
58 min
Hacking how we see
A way to fix lazy eye?
38 min
Open-BCI DIY-Neuroscience Maker-Art Mind-Hacking
open source DIY brain-computer-interfaces | technology and…

13 min
OpenQA - review jobs and file bug report
OpenSUSE job review/bug report

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

51 min