Search for "11" returned 4572 results

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache
43 min
WTF DJI, UAV CTF?!
A hacker's view at commercial drone security

61 min
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…
64 min
Der Deep Learning Hype
Wie lange kann es so weitergehen?
60 min
„Nach bestem Wissen und Gewissen“ – Floskeln in der Politik
Politische Phrasologie – warum man aus dem ganzen Zeug, das…

60 min
Ich sehe, also bin ich ... Du
Gefahren von Kameras für (biometrische)…
47 min
All cops are broadcasting
Obtaining the secret TETRA primitives after decades in the…

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…
61 min
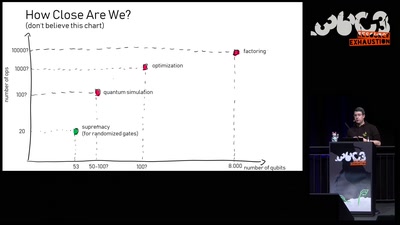
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

54 min