Search for "16" returned 4642 results

60 min
Ich sehe, also bin ich ... Du
Gefahren von Kameras für (biometrische)…

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

38 min
Content take-downs: Who cleans the internet?
EU plans to swipe our freedom of expression under the carpet

58 min
SpiegelMining – Reverse Engineering von Spiegel-Online
Wer denkt, Vorratsdatenspeicherungen und „Big Data“ sind…
39 min
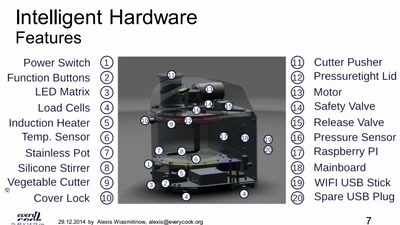
Why do we need an open food information platform
We want all data about food to be linked and public

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy

95 min
The Time is Right
Ein Science-Fiction-Theaterstück

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

53 min