Search for "16" returned 4517 results

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

60 min
Ich sehe, also bin ich ... Du
Gefahren von Kameras für (biometrische)…

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache
82 min
Rückkanal bei der Podcasterei:
Twitter ist tot, Es lebe das Fediverse?!

95 min
The Time is Right
Ein Science-Fiction-Theaterstück

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…
61 min
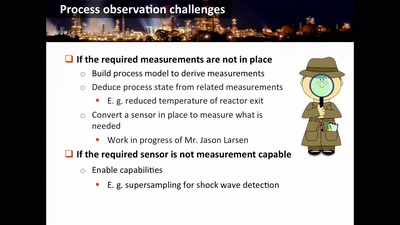
Damn Vulnerable Chemical Process
Exploitation in a new media
61 min
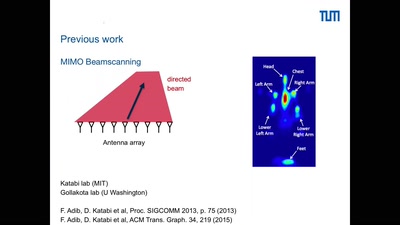
Holography of Wi-Fi radiation
Can we see the stray radiation of wireless devices? And…

54 min