Search for "29" returned 4233 results

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy
60 min
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

62 min
radare demystified
after 1.0

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…
46 min
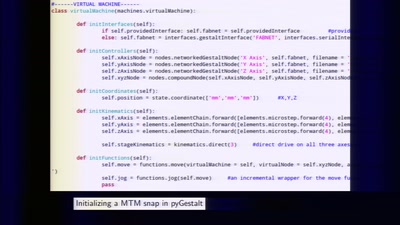
Making machines that make
rapid prototyping of digital fabrication and…

59 min
Zwischen supersicherer Verschlüsselung und Klartext liegt nur ein falsches Bit
Ein Streifzug durch die Fehler in der Kryptografie

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

63 min
Building Custom Pinball Machines
What you need and how it works. An experiences report

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption
47 min
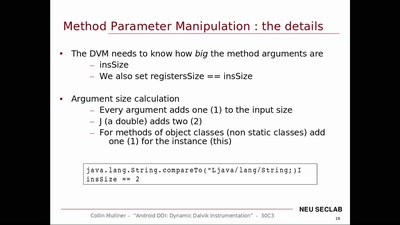
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…

62 min
Let's Encrypt
A Free Robotic Certificate Authority

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

51 min