Search for "29" returned 4232 results

31 min
TrustZone is not enough
Hijacking debug components for embedded security

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

61 min
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…

63 min
Don't stop 'til you feel it
Artistic interventions in climate change

57 min
Du kannst alles hacken – du darfst dich nur nicht erwischen lassen.
OpSec für Datenreisende

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?
61 min
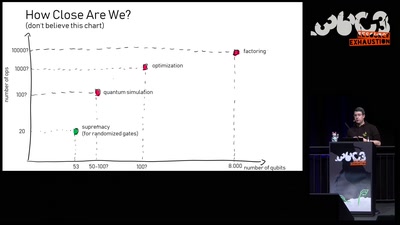
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

60 min
Ich sehe, also bin ich ... Du
Gefahren von Kameras für (biometrische)…

14 min
c3 NewsShow
Tag 1

66 min
Keine Anhaltspunkte für flächendeckende Überwachung
Die Diskussion um NSA, PRISM, Tempora sprachlich und…

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology
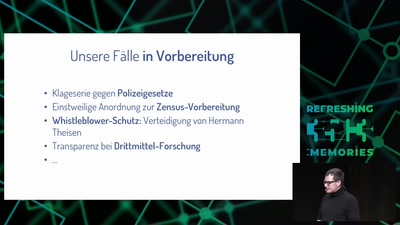
60 min