Search for "13" returned 4825 results

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

29 min
Es sind die kleinen Dinge im Leben II
was alles geht und wie man anfängt, mit Mikroskopen

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

36 min
Modchips of the State
Hardware implants in the supply-chain

62 min
Deine Rechte sind in diesen Freihandelsabkommen nicht verfügbar
Der Protest gegen TTIP und CETA
31 min
Trackography
You never read alone
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

57 min
Make Wi-Fi fast again
Eine kleine Einführung in den 802.11ac Standard

26 min
Opening Event
35C3: Refreshing Memories
31 min
Berechnete Welt
Unsere Daten, die Zukunft und die zerstörte Demokratie

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security
58 min
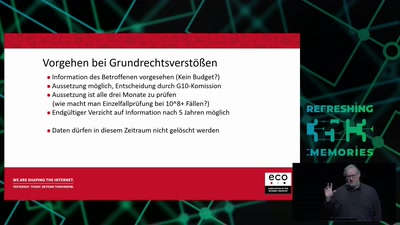
G10, BND-Gesetz und der effektive Schutz vor Grundrechten
Die strategische Fernmeldeüberwachung des BND vor dem…
22 min