Search for "17" returned 4689 results

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?
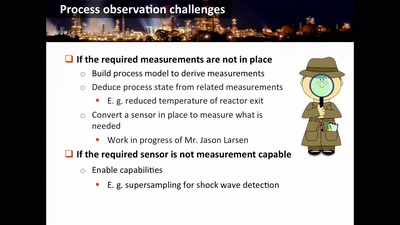
61 min
Damn Vulnerable Chemical Process
Exploitation in a new media
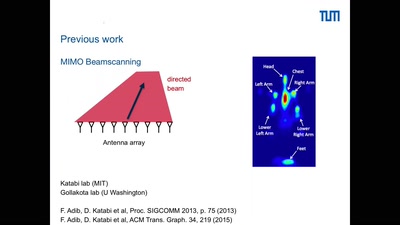
61 min
Holography of Wi-Fi radiation
Can we see the stray radiation of wireless devices? And…

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy
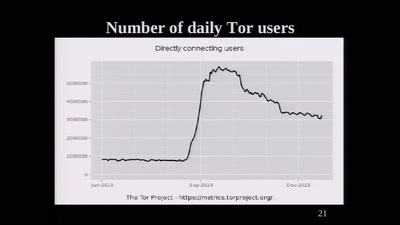
62 min
The Tor Network
We're living in interesting times

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap
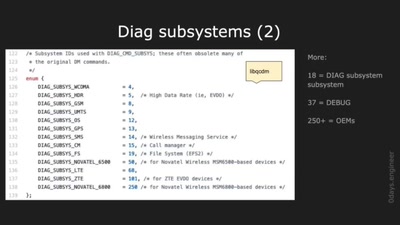
66 min
Advanced Hexagon Diag
Harnessing diagnostics for baseband vulnerability research

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

38 min