Search for "42" returned 3654 results

62 min
Was schützt eigentlich der Datenschutz?
Warum DatenschützerInnen aufhören müssen von individueller…

58 min
Open Source Estrogen
From molecular colonization to molecular collaboration
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!
59 min
Computer, die über Asyl (mit)entscheiden
Wie das BAMF seine Probleme mit Technik lösen wollte und…

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

11 min
c3 NewsShow
Tag 2

60 min
Shopshifting
The potential for payment system abuse

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…
61 min
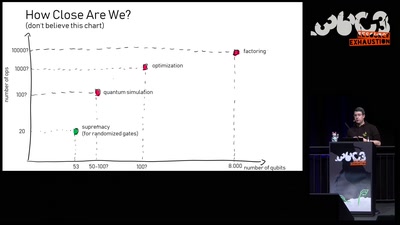
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

57 min
Du kannst alles hacken – du darfst dich nur nicht erwischen lassen.
OpSec für Datenreisende
61 min
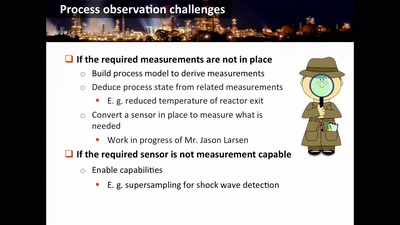
Damn Vulnerable Chemical Process
Exploitation in a new media

54 min