Search for "15" returned 4786 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
42 min
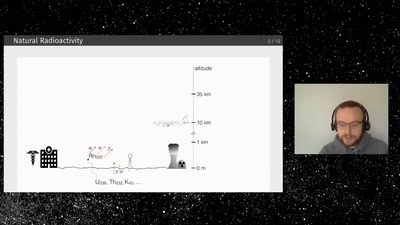
Measuring radioactivity using low-cost silicon sensors
A DIY particle physics detector in a tin box.

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

13 min
OpenQA - review jobs and file bug report
OpenSUSE job review/bug report

46 min