Search for ".had" returned 5386 results

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…
60 min
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development
60 min
Building knodium.com with Scheme
First-hand experience report of a business application…

56 min
#NoEstimates
Why estimates are bad for your software & team & management
55 min
Lobby-Schlacht um die ePrivacy-Verordnung
Die EU hat die Wahl: Schutz von Menschen oder von…

63 min
50 years in filesystems
Writing data to disk – how hard can it be, and what have we…
37 min
Ansible all the Things
No, i don't want to install Jitsi the 100th time by hand
40 min
Improving security with Fuzzing and Sanitizers
Free and open source software has far too many security…
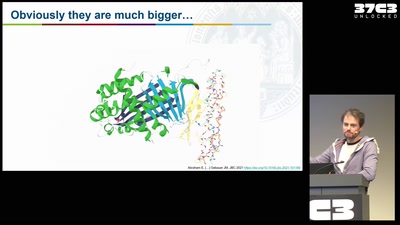
61 min
AlphaFold – how machine learning changed structural biology forever (or not?)
Getting first-hand insights into the impact of machine…

63 min
Data Exploitation
how your digital doppelganger has been exploiting you all…
33 min
Open Source: A question of national and global security
What will you do when things go bad? Taking precautions in…

38 min
Zapfenstreich
Über Algorithmen im Krieg, aber was hat die Kunst damit…

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

32 min
Live: Avahi / Zeroconf: Some magic sauce that's about more than files and printers
Hand editing config files for local deployment? Say hi to…

47 min
The KGB Hack: 30 Years Later
Looking back at the perhaps most dramatic instance of…

53 min
A Case Against C++
Why C++ is bad for the environment, causes global warming…
21 min
Designing PCBs with code
Is designing circuits with code instead of CAD the future…
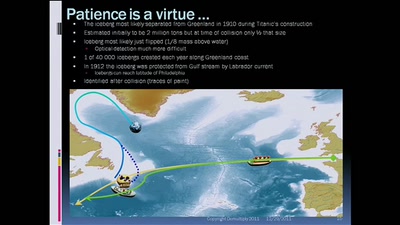
56 min
The future of cryptology: which 3 letters algorithm(s) could be our Titanic?
RMS Olympic, RMS Titanic, HMHS Britannic vs Discrete…

63 min