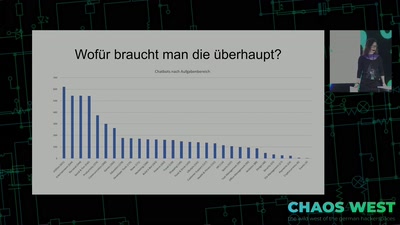
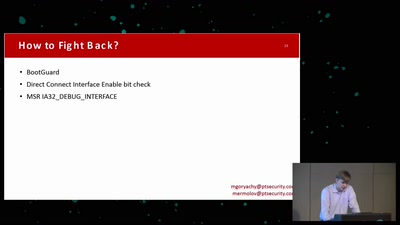
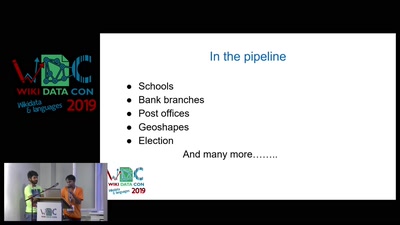
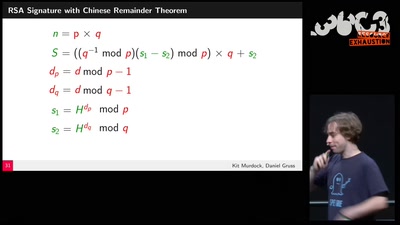
Search for "876" returned 1862 results

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study

53 min
Cryptography demystified
An introduction without maths

60 min
Profiling (In)justice
Disaggregating Data by Race and Ethnicity to Curb…

31 min
Sysadmins of the world, unite!
a call to resistance

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
60 min
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

66 min
The Snowden Refugees under Surveillance in Hong Kong
A Rapidly Emerging Police State and Imminent Deportation to…

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

34 min