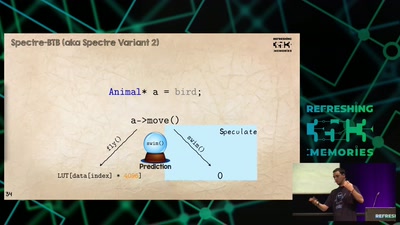
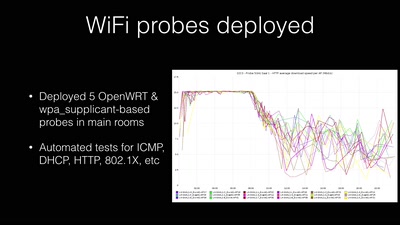
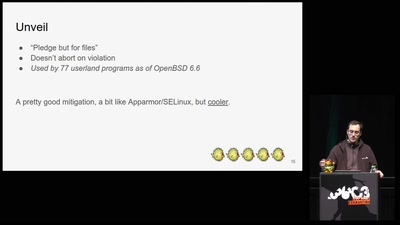
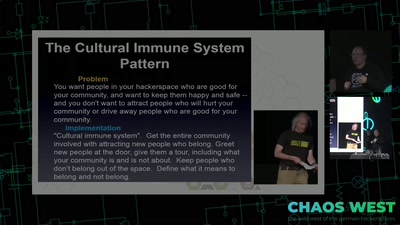
Search for "358" returned 2027 results
60 min
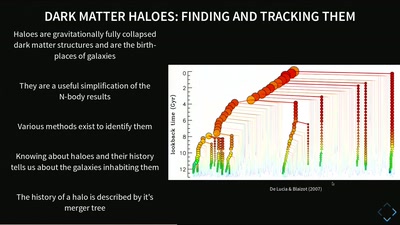
Simulating Universes
What Virtual Universes Can Tell Us About Our Own

60 min
Lets break modern binary code obfuscation
A semantics based approach

62 min
radare demystified
after 1.0

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

55 min
3D Casting Aluminum
Too Much Fun with Microwaves

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs
61 min
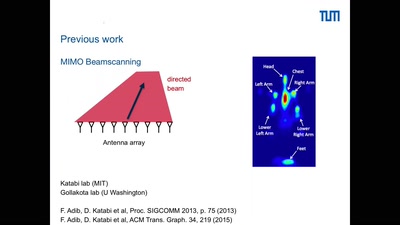
Holography of Wi-Fi radiation
Can we see the stray radiation of wireless devices? And…

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

55 min
Attribution revolution
Turning copyright upside-down with metadata
56 min
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming

58 min
07KINGSTON25 JAMAICA: MALARIA UPDATE Dispatches from Fort Meade
Reporting on the secret trial of Chelsea Manning
61 min