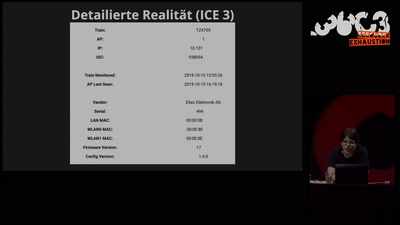
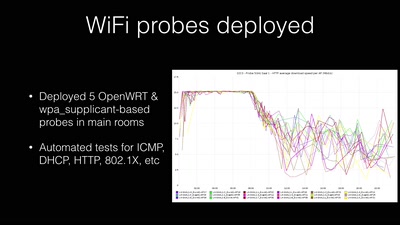
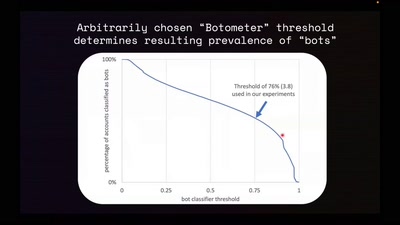
Search for "374" returned 1967 results

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

58 min
Switches Get Stitches
Industrial System Ownership

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

35 min
Internet of toilets
Trends in the sanitarian territory
62 min
Internet, the Business Side
a try to explain the ecosystem
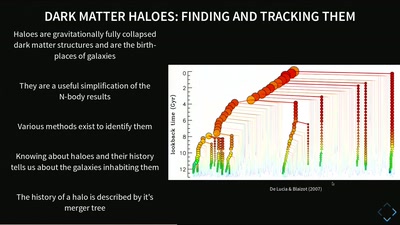
60 min
Simulating Universes
What Virtual Universes Can Tell Us About Our Own

60 min
Lets break modern binary code obfuscation
A semantics based approach

62 min
radare demystified
after 1.0

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?
36 min