Search for "547" returned 1907 results

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache
58 min
G10, BND-Gesetz und der effektive Schutz vor Grundrechten
Die strategische Fernmeldeüberwachung des BND vor dem…

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

61 min
Beeinflussung durch Künstliche Intelligenz
Über die Banalität der Beeinflussung und das Leben mit…
52 min
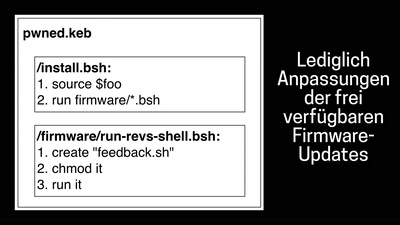
Ladeinfrastruktur für Elektroautos: Ausbau statt Sicherheit
Warum das Laden eines Elektroautos unsicher ist

63 min
Reconstructing narratives
transparency in the service of justice
41 min
Demoscene now and then
The demoscene is an underground computer art culture.

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

58 min
When hardware must „just work“
An inside look at x86 CPU design

58 min
Baseband Exploitation in 2013
Hexagon challenges

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

60 min
Concepts for global TSCM
getting out of surveillance state mode

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

62 min