Search for "858" returned 1877 results
113 min
Das Bits&Bäume-Sporangium
8 Mikrokosmen, 8 Expert*innen, je 8 Minuten zu…

30 min
On Computing Numbers, with an Application to Problems of our Society
Journalism ♥ Computer Science

62 min
To Protect And Infect, Part 2
The militarization of the Internet

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it
61 min
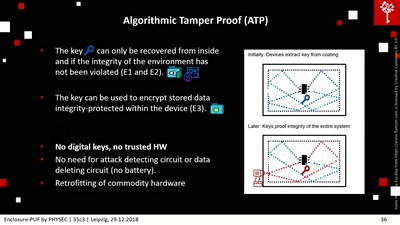
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…

62 min
Transhuman Expression
Interdisciplinary research in Painting and Robotics. with…

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

72 min
Console Hacking
Breaking the 3DS

62 min
HUMUS sapiens
Open Soil Research

56 min
Viva la Vita Vida
Hacking the most secure handheld console
60 min
Desperately Seeking Susy
A farewell to a bold proposal?

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

55 min
White-Box Cryptography
Survey

61 min
Safe and Secure Drivers in High-Level Languages
How to write PCIe drivers in Rust, go, C#, Swift, Haskell,…
64 min

![Why we are addicted to lithium [1/2]](https://static.media.ccc.de/media/events/rc3/2021/193-3fd1b8af-9ab6-54c5-88ad-2622c1cc925a.jpg)