Search for "854" returned 1901 results

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?
44 min
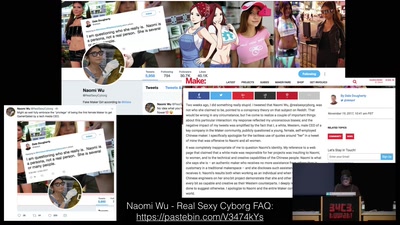
Replication Prohibited
3D printed key attacks

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

90 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…
56 min
Deconstructing a Socialist Lawnmower
Obsolete Technologies + Critical Material Studies in Media…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

55 min
Attribution revolution
Turning copyright upside-down with metadata

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…

57 min
Theater und Quantenzeitalter
„Die Parallelwelt“- Das Schauspiel Dortmund und die…

62 min
HUMUS sapiens
Open Soil Research
61 min
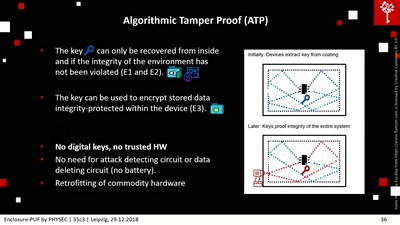
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications
59 min
NSA Points of Presence in AT
Vortrag mit aktuellen Fotos aus luftigen Perspektiven

59 min
Provable Security
How I learned to stop worrying and love the backdoor

65 min
The Untold Story of Edward Snowden’s Escape from Hong Kong
and How You Can Help the Refugees Who Saved His Life

58 min
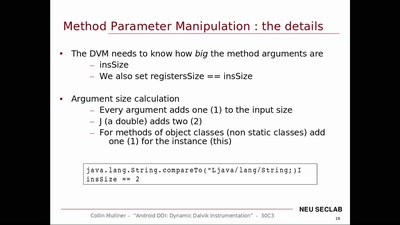
PLC-Blaster
Ein Computerwurm für PLCs
47 min