Search for "Lisa" returned 984 results

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…
63 min
Das Assange-Auslieferungsverfahren
Als Prozessbeobachter in London

58 min
Skynet Starter Kit
From Embodied AI Jailbreak to Remote Takeover of Humanoid…

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

47 min
The KGB Hack: 30 Years Later
Looking back at the perhaps most dramatic instance of…

59 min
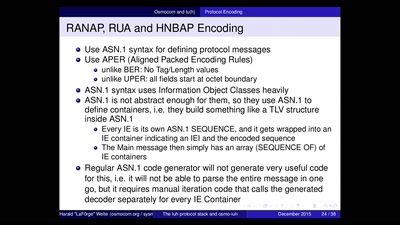
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security
56 min
Running your own 3G/3.5G network
OpenBSC reloaded

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage
25 min
Saving the World with Space Solar Power
or is it just PEWPEW?!
47 min
Jailbreaking iOS
From past to present
31 min
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…
43 min
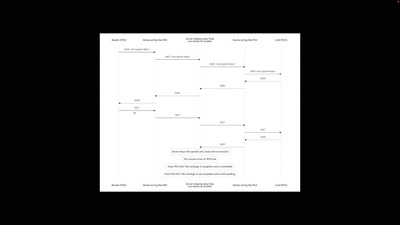
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

61 min