Search for "big data"
prev
next

60 min
Efail, other attacks and lessons learned.

33 min
Intrusion and Exfiltration in Server-less Architectures
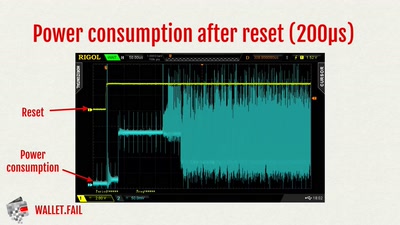
61 min
Hacking the most popular cryptocurrency hardware wallets

55 min
Attribute Based Credentials in Practice

63 min
how the EU was hypnotised that the NSA did not exist

35 min
Trends in the sanitarian territory
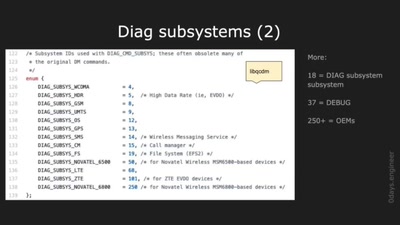
66 min
Harnessing diagnostics for baseband vulnerability research

59 min
A Journey in the Land of (Cyber-)Espionage

30 min
Reversing the Surveillance Business Model
43 min
It is just a broken memcpy in the Bluetooth stack. Do we…
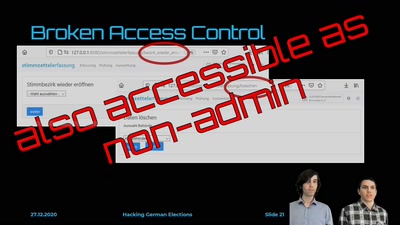
63 min
Insecure Electronic Vote Counting - How It Returned and Why…

62 min
The militarization of the Internet
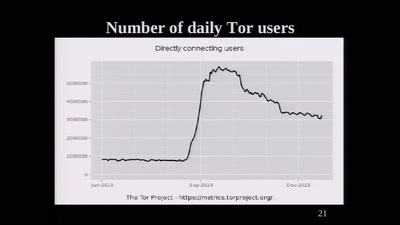
62 min
We're living in interesting times
38 min
Explaining in detail just how those little COM files…

55 min
A gentle introduction to elliptic-curve cryptography

53 min
Uncovering Nation-State Mobile Espionage in the Wild
prev
next








