Search for "16" returned 4652 results
31 min
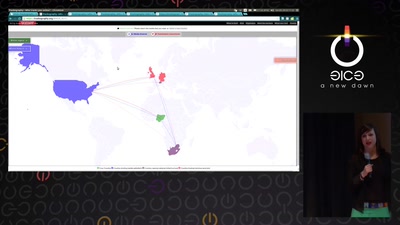
Trackography
You never read alone

46 min
CounterStrike
Lawful Interception
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

63 min
Reconstructing narratives
transparency in the service of justice

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics
32 min
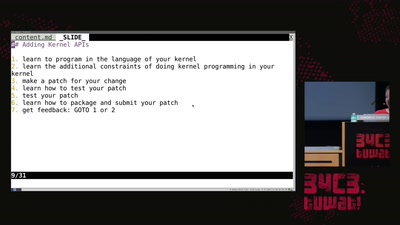
library operating systems
reject the default reality^W abstractions and substitute…
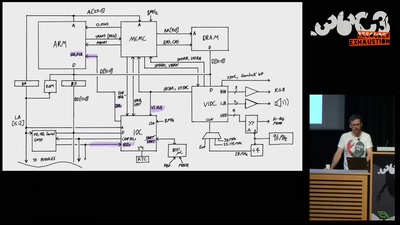
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

58 min
Funkzellenabfrage: Die alltägliche Rasterfahndung unserer Handydaten
Wie wir alle regelmäßig den Behörden ins Netz gehen und wie…

34 min
Social Cooling - big data’s unintended side effect
How the reputation economy is creating data-driven…
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online
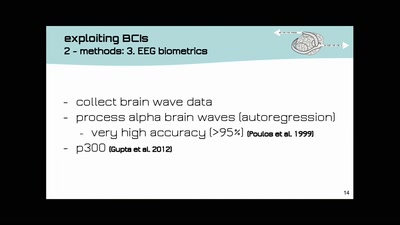
38 min
Open-BCI DIY-Neuroscience Maker-Art Mind-Hacking
open source DIY brain-computer-interfaces | technology and…

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…

30 min