Search for "10" returned 5091 results

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…

58 min
Baseband Exploitation in 2013
Hexagon challenges

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…
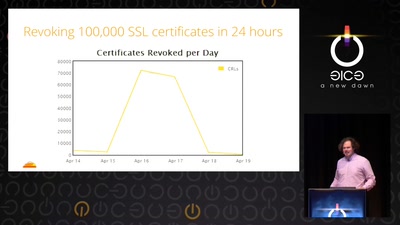
29 min
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…
27 min
Maritime Robotics
Hackers, I call thee to our Oceans!

44 min
Genom-Editierung mit CRISPR/Cas
“Eine neue Hoffnung” oder “Angriff der Klonkrieger”?

60 min
Hacking Reality
Mixed Reality and multi-sensory communication

63 min
goto fail;
exploring two decades of transport layer insecurity

30 min
OONI: Let's Fight Internet Censorship, Together!
The Open Observatory of Network Interference

60 min