Search for "16" returned 4678 results
58 min
CHINTERNET ART
Creativity, Archives & Digital Media from the Chinese…

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics
55 min
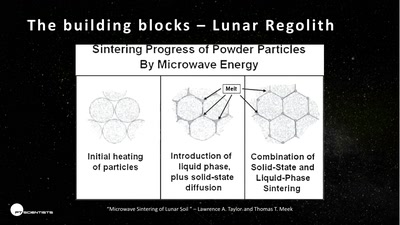
3D printing on the moon
The future of space exploration

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…
32 min
library operating systems
reject the default reality^W abstractions and substitute…

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

45 min
To Protect And Infect
The militarization of the Internet

58 min
Funkzellenabfrage: Die alltägliche Rasterfahndung unserer Handydaten
Wie wir alle regelmäßig den Behörden ins Netz gehen und wie…

60 min
Mein Bot, der Kombattant
Operative Kommunikation im digitalen Informationskrieg

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…

67 min
The Maker movement meets patent law
How many windows are open in the patent fortress

61 min