Search for "15" returned 4930 results
44 min
Replication Prohibited
3D printed key attacks

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…
59 min
Scientific Literacy 101
Let's understand how the scientific system works

60 min
Shopshifting
The potential for payment system abuse

61 min
Zamir Transnational Network und Zagreb Dairy
Das erste computer netzwerk in Krieg (Jugoslavia 1992-1997)

61 min
"The" Social Credit System
Why It's Both Better and Worse Than We can Imagine

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

42 min
Code for Climate – Was 2020 bei Code for Germany passiert
Offene Daten können helfen, das Klima zu schützen.
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy
63 min
Kritikalität von Rohstoffen - wann platzt die Bombe?
Ein nicht nuklearer Blick auf das Ende der Welt

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…
54 min
How medicine discovered sex
Introduction to sex- and gender-sensitive medicine
36 min
Artistic PCB Design and Fabrication
From doodle to manufacture: how I make mechanically…

46 min
The nextpnr FOSS FPGA place-and-route tool
the next step forward in open source FPGA tools
65 min
LatticeHacks
Fun with lattices in cryptography and cryptanalysis
42 min
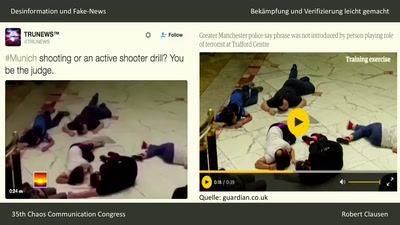
Desinformation und Fake News
Bekämpfung und Verifizierung leicht gemacht

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…
42 min