Search for "12" returned 4995 results

45 min
To Protect And Infect
The militarization of the Internet

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

58 min
Switches Get Stitches
Industrial System Ownership

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…
55 min
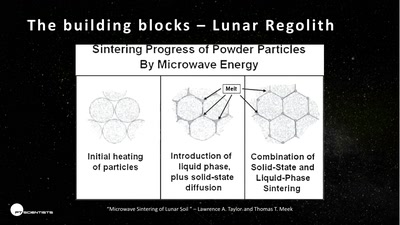
3D printing on the moon
The future of space exploration
67 min
Mit Kunst die Gesellschaft hacken
Das Zentrum für politische Schönheit

61 min
Quantenphysik und Kosmologie
Eine Einführung für blutige Anfänger

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

51 min
How to contribute to make open hardware happen
Mooltipass, Openpandora/Pyra and Novena/Senoko: how I…

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
46 min