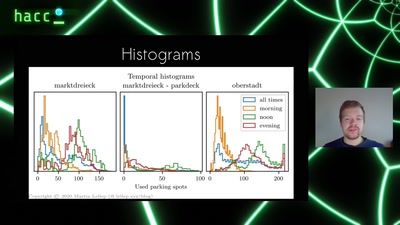
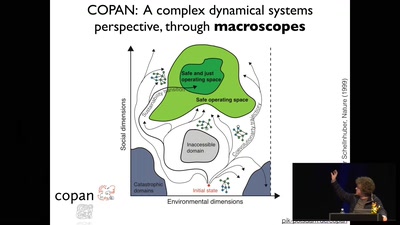
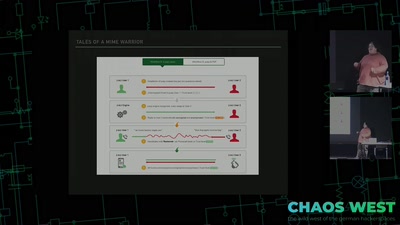
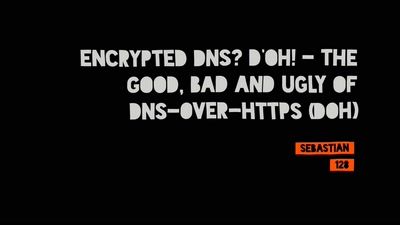
Search for "25" returned 4560 results

59 min
Provable Security
How I learned to stop worrying and love the backdoor

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…
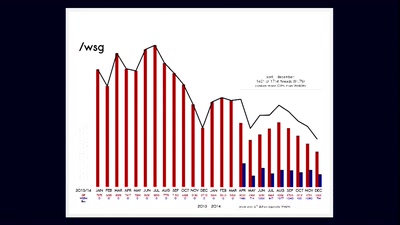
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

32 min
History and implications of DRM
From tractors to Web standards

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

60 min
Best of Informationsfreiheit
Transparenz mit der Brechstange

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!
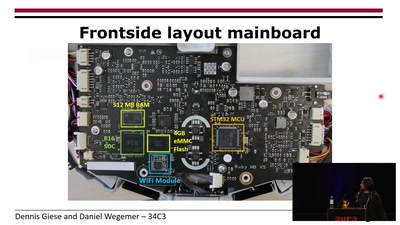
31 min
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

43 min
How Facebook tracks you on Android
(even if you don’t have a Facebook account)

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy

62 min
SymbiFlow - Finally the GCC of FPGAs!
A fully FOSS, Verilog to bitstream, timing driven, cross…

60 min
Lets break modern binary code obfuscation
A semantics based approach
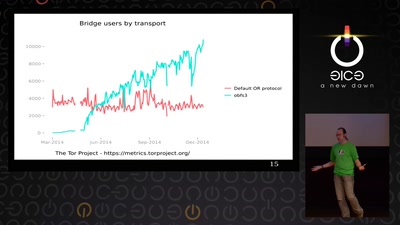
72 min
State of the Onion
Neuland

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster
27 min
Maritime Robotics
Hackers, I call thee to our Oceans!

55 min