Search for "19" returned 4609 results

42 min
A world without blockchain
How (inter)national money transfers works

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…
49 min
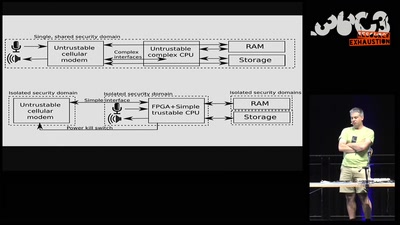
Creating Resilient and Sustainable Mobile Phones
Be prepared for the coming Digital Winter. And play…
64 min
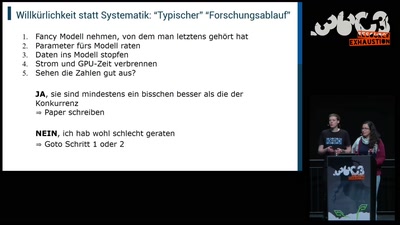
Der Deep Learning Hype
Wie lange kann es so weitergehen?

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
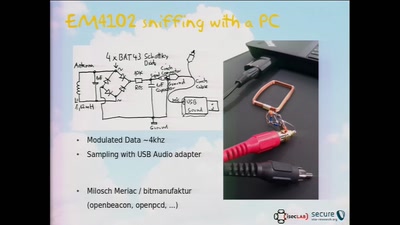
58 min
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems

60 min
Ich sehe, also bin ich ... Du
Gefahren von Kameras für (biometrische)…
61 min
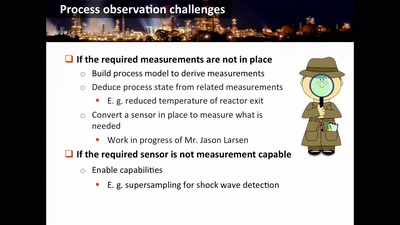
Damn Vulnerable Chemical Process
Exploitation in a new media

60 min
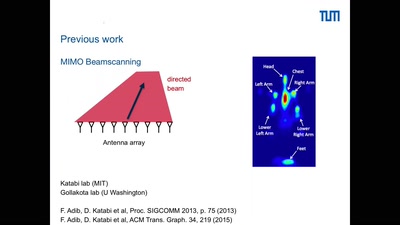
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…
61 min